ogmini - Exploration of DFIR
Having fun while learning about and pivoting into the world of DFIR.
About Blog Posts by Tags Research Talks/Presentations GitHub RSS
POC Malware - Part 1
by ogmini
Gaslitpad is the name of the POC malware that I’m currently working on. It is the result of my ongoing research into Windows Notepad at https://github.com/ogmini/Notepad-State-Library. The general idea is a program that sits in wait and changes the unsaved buffer for nefarious purposes.
Scenario
A sysadmin is in the process of editing a remote configuration file, makes some changes, saves the file, and walks away from the computer for a moment without closing Windows Notepad. After a minute, the Windows Notepad window blinks and no one notices. A change has been made and the file needs to be saved again.

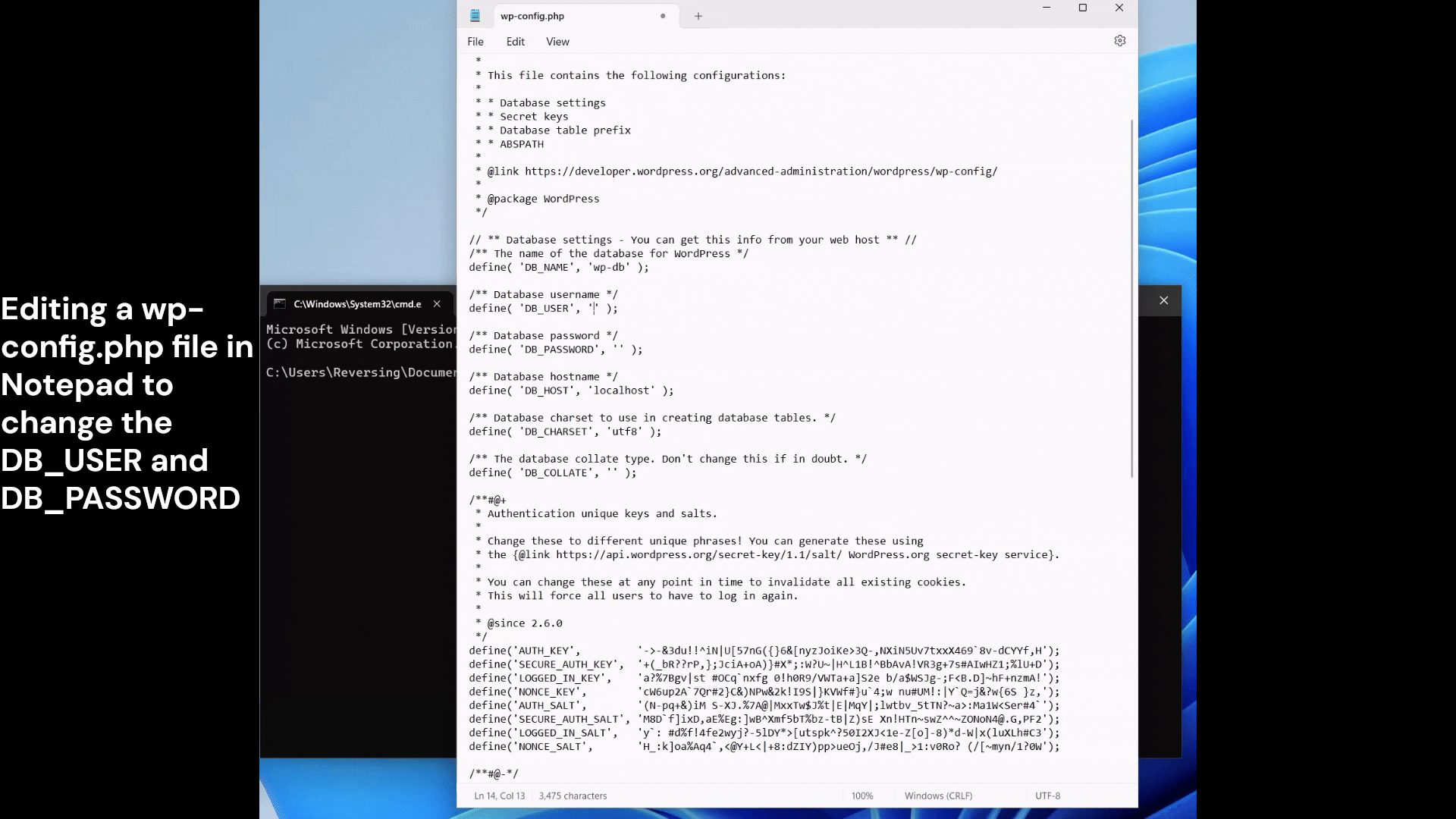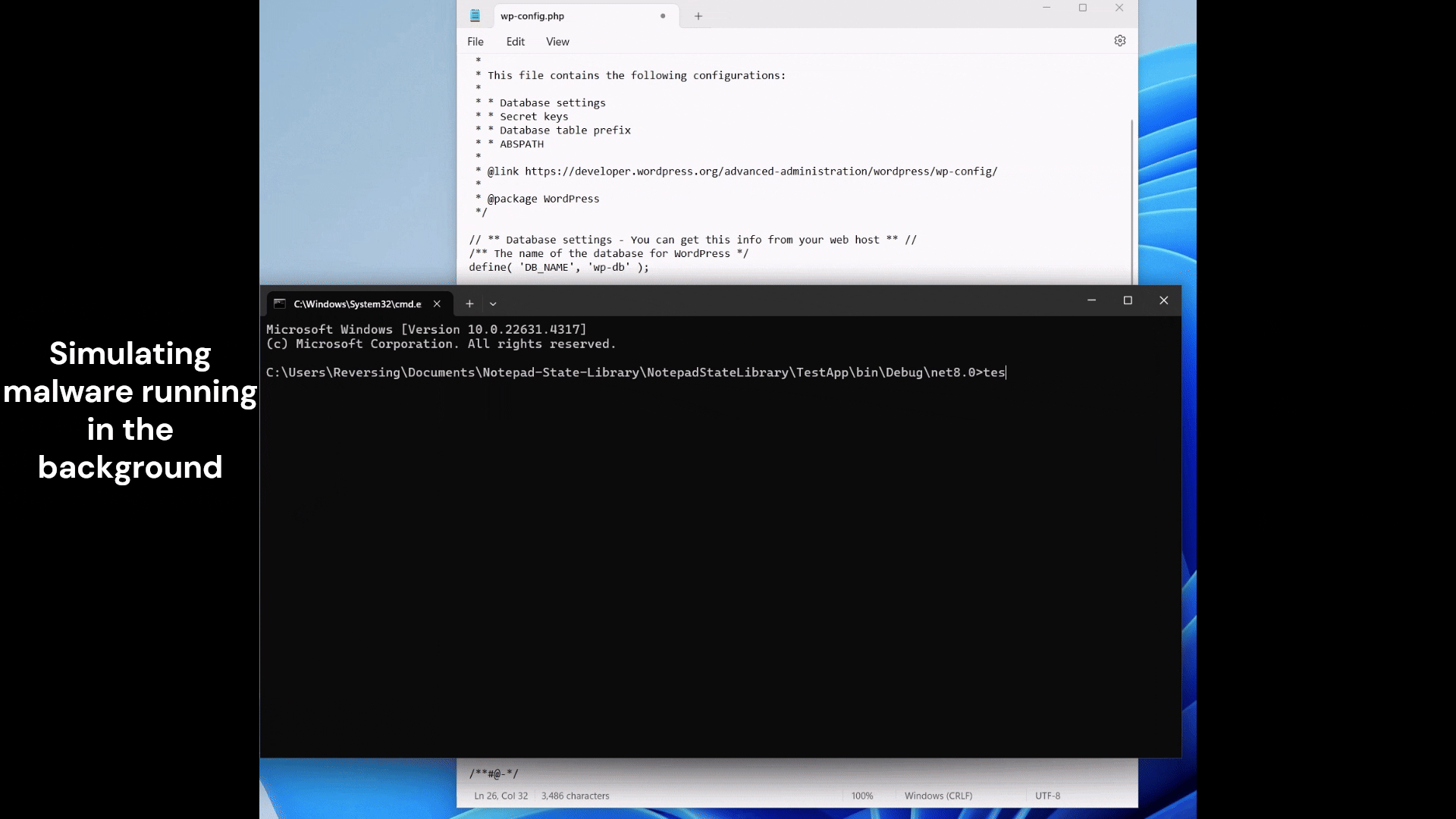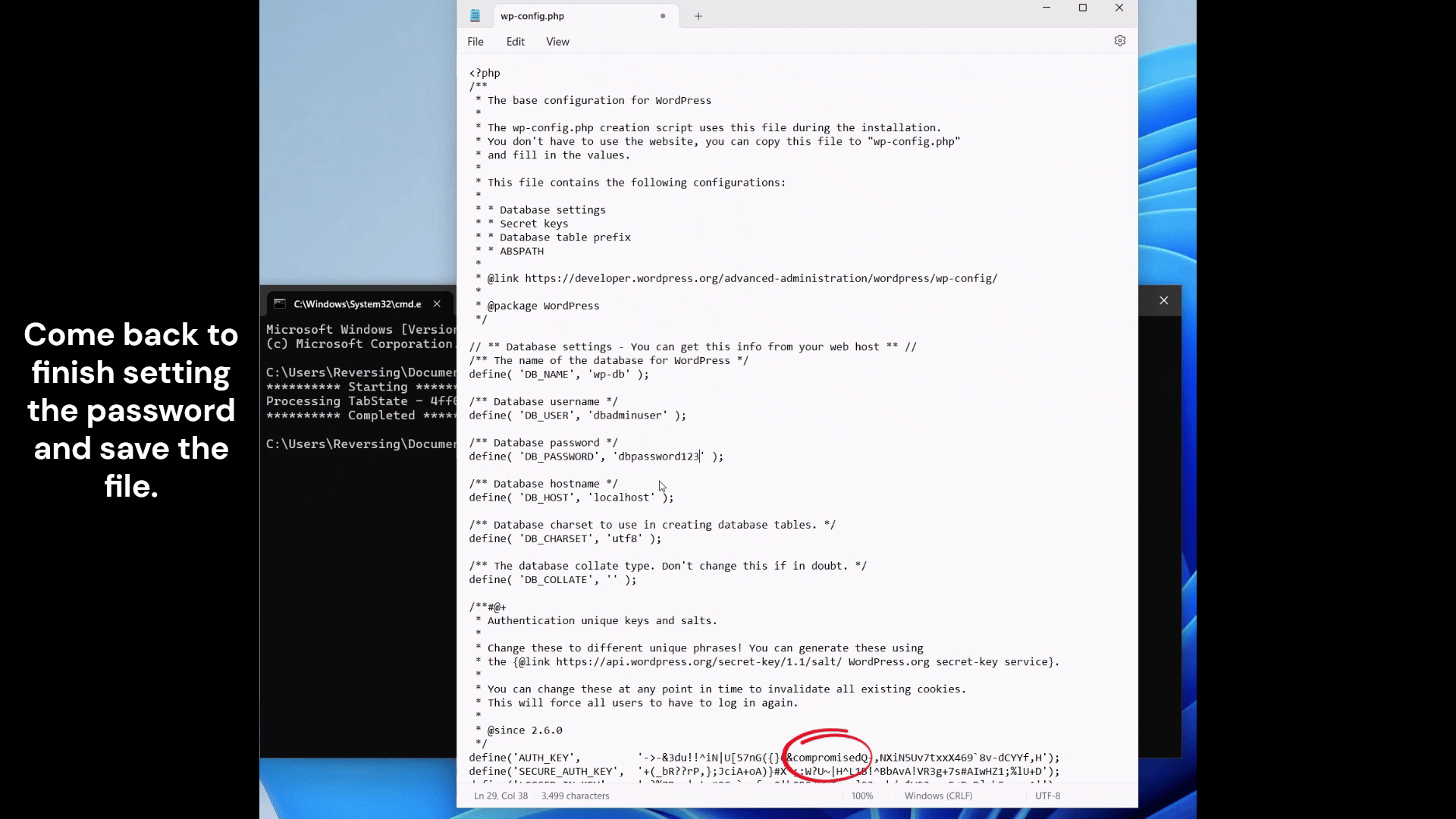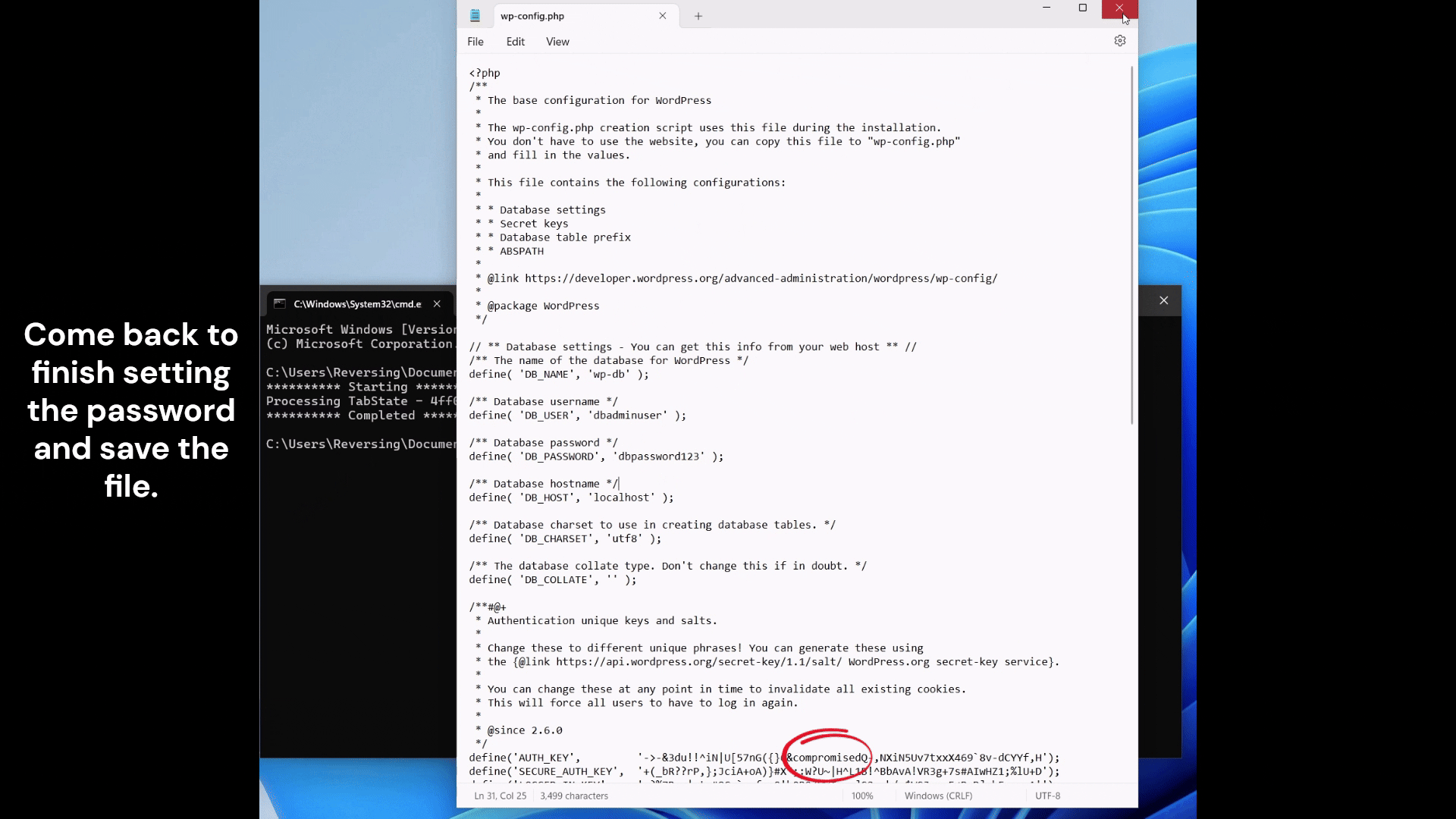
Our poor overworked sysadmin thinks to themselves, I guess I didn’t save my changes. Presses Ctrl-S and saves the malicious change.
There are also slight variations on this scenario and how the POC malware could work. The end goal and result is to cause the enduser to save malicious changes to files opened in Windows Notepad.
Progress
I currently have a very hardcoded version that sits and waits for a wp-config.php file to be opened. It proceeds to change the AUTH_KEY and other important keys to known values. The following post explains the importance of these values https://blog.sucuri.net/2023/06/what-are-wordpress-salts-security-keys.html
Future Plans
I want to clean up the code and make it a little more robust and maybe a little more generic. Something that maybe a Red Team could use.
A simpler POC malware would just listen for files to be opened and ship out the information to a bad actor. Essentially a keylogger. I might also write this one up.
I do not intend on trying to obfuscate or hide the actions of this POC malware.
tags: #Malware