Magnet Virtual Summit 2026 CTF - AAR "Welcome Home"
Having fun while learning about and pivoting into the world of DFIR.

This year I’m going to writeup AARs for the challenges that I solved differently from Hexordia or felt needed to be expanded upon due to my approach or thinking. The first one is “That’s not a Mario character”.

It has already been a year since my first participation in the Magnet Virtual Summit 2026 CTF. If you haven’t signed up, it isn’t too late! https://mvs2026.ctfd.io/
Forgive the late recap! To say that the last 2 months have been busy and full of change would be an understatement. Back at the start of 2025, David Cowen put forth the Zeltser Challenge. I jumped in and this post will provide a little recap of highlights and what I got out of the challenge. Not everything went according to plan.
Christian Peter announced https://www.linkedin.com/posts/christian-peter-49b4ab182_alex-aleapp-forensics-activity-7401344010373451776-Il3H the addition of support for rooted Android devices for ALEX - available at https://github.com/prosch88/ALEX. I wanted to give the new functionality a try to see how it works as ALEX has been a great tool when doing research and testing.
Came across an interesting SQLite database called cpe.db on the mobile hotsport as I was starting to examine all the files under the /usrdata/data/usr folder. It contained old SMS messages! In my case, these were spam SMS messages that I had ignored and never bothered to read/delete when I was still using this hotspot actively.
Still looking at the Orbic Speed RC400L hotspot. You can find all the previous posts at https://ogmini.github.io/tags.html#Mobile-Hotspot. Today, I started looking at the various log files located at /data/logs.
Continuing to examine the Orbic Speed RC400L for any interesting digital artifacts from last post. I’m interested in finding digital artifacts that can help place the hotspot in a place and time and also devices that connect to the hotspot. Possibly seeing if/how it logs connections to cell towers.
I’ve been following the Rayhunter project from EFF over at https://github.com/EFForg/rayhunter. I’ve had and used an Orbic Speed RC400L as a mobile hotspot for many years. I recently replaced it with a 5G compatible hotspot for the speeeeeeeeeeeeeed. I actually hate the newer one as it boots up way slower. Either way, I have an unused Orbic Speed RC400L hotspot now that is ripe for playing around with. While researching Rayhunter, I was interested in what digital artifacts could be recovered from a stock device. The project to install Rayhunter was put on hold for this.
Been enjoying the SANS Holiday Hack Challenge 2025! Got past Act 1 and I’ve finished 2/7 of Act 2. We can’t do any write ups yet so I’ll talk in general terms about my impressions so far.
I somehow missed that this was starting already. The SANS Holiday Hack Challenge 2025 is live now at https://www.sans.org/cyber-ranges/holiday-hack-challenge#play. We’ll see how far I can get this year. This is more of a general Cybersecurity CTF as opposed to a Digital Forensic CTF. I do like that they added a “CTF Style” as it was kind of tedious moving around the map. I can just focus on the challenges.
Trying out Android Logical Extractor (ALEX) by Christian Peter today — available at https://github.com/prosch88/ALEX. My test setup:
Belkasoft recently launched some new training related to effectively using AI in DFIR. https://www.linkedin.com/posts/belkasoft_dfir-digitalforensics-ai-activity-7390772730951839744-fZum?. When I signed up the course was free for a short time. I’m intrigued to see how the course presents using AI. I continue to be very cautious about AI and its use. Both from an environmental and human impact viewpoint. After I complete the course I will be sure to post my thoughts.
As I was reading This Week in 4N6, I came across a great article from Adam Hachem at https://www.hexordia.com/blog/using-open-source-forensic-tools. I would encourage you to read it especially if you aren’t a Python pro. When I first started playing around with Python, it took me too long to fully embrace the usefulness of venv or Virtual Environments. If you don’t know venv, this is your cue to go read the article!
Looking back on October had me diving heavily into Android Forensics. I also of course gave my talk at BSides NYC 0x05. Wasn’t the best talk as I had some mic issues,talked way too fast, and missed some of my keypoints; but I learned a lot and it was an enjoyable experience. Hopefully this won’t be my last. The volunteers and organizers do an amazing job at running the event.
Windows 11 25H2 started being pushed out as an update in October 2025 and today we’re going to be looking if anything has changed with Windows Notepad version 11.2507.26.0. This is what I’ve found/noticed so far:
Recently stumbled upon something to make my life easier as I find myself spinning up VMs on Hyper-V constantly to perform testing and validation. I prefer to have completely clean installs and tend to not reuse a VM for later testing. This can result in a sort of “blindspot” to finding artifacts on an actually “used” computer. This post isn’t about that though. When creating my VMs I have always made use of Answer files to automate the installation and configuration to reduce human error and increase repeatability. You can use https://schneegans.de/windows/unattend-generator/ to generate different Answer files.
Over the last few months, I’ve been doing collaborative research with reece394 over on GitHub. They made a recent feature request on the Registry Hunter repo https://github.com/Velocidex/registry_hunter/issues/21#issuecomment-3427299524 which encapsulates everything we’ve both researched so far very well. Mari Degrazia also has a very good write up over at https://www.zerofox.com/blog/the-registry-hives-you-may-be-msix-ing-registry-redirection-with-ms-msix/ about the growing importance of these artifacts. Chris Ray over at Cyber Triage has also mentioned it previously at https://www.cybertriage.com/blog/ntuser-dat-forensics-analysis-2025/.
Late recap for September. We’re almost done with October at this point! A bunch of missed posts; but, September is one of the busiest months for work as it is the start of a new academic year.
Releasing Version 1.0.5 of Windows Notepad Parser https://github.com/ogmini/Notepad-State-Library/releases/tag/v1.0.5. This is a bug/security fix release.
BSides NYC 0x05 hosted a few different CTFs and CTFd put a call out for volunteers to submit a few CTF Challenges. I decided to give it a shot and submitted three forensic type challenges. It was a fun experience as I have never written a CTF challenge. The CTFd people were a great bunch to work with!
Coming off yesterday’s post, I wrote up a quick Python script to generate and pull a tar file from a rooted Android phone. Nothing fancy, but it helps speed up my research/testing process. You can pass it a path on the Android phone and it will tar up the folder. Example would be passing it /data/data/dji.go.v5. You can also pass it an output path to save the tar file on to secondary storage or somewhere on internal storage. This adds a second script to my “collection” on https://github.com/ogmini/Forensic-ADB-Scripts.
Recently picked up a cheap DJI Neo to play around. I have to say they’re pretty cheap and easy to use. I installed the DJI Fly software on my “research” Pixel 7 because there is no way I’m installing that app on my real phone. Might as well dig into its artifacts! I imagine this has already been done and written up. I haven’t looked heavily yet for prior research. Either way, it is good practice to go artifact hunting with minimal prior information. What follows are just some quick notes as I poke around.
What follows is the “written” version of my talk at BSides NYC 0x05. I still find writing a better way to disseminate information. Talks are also fun for the person to person interaction. This writeup removes some of the fluff from the talk.
Finally got around to finishing up a Python script that I am creatively calling “adb-pull-stat.py” that I talked about in a previous post. It is nothing fancy and was written to fill a need I had. The script has been published to a GitHub repo - https://github.com/ogmini/Forensic-ADB-Scripts. I have a sneaky feeling that I might be writing more “utility” scripts as I continue looking and Android devices and they’ll be finding their way into that repo.
This post will show why focused, repeatable testing is so important. Yesterday’s post hinted at some possible message logging tables in one of the sqlite databases. I had come across entries while testing for attachments that I had not seen previously. Initially, I had chalked that up to not having sent any emails to the Trash folder until I wanted to test what happened to cached attachments. Well…
Just put in the PR to update the ALEAPP plugin to handle attachments. Details about attachments can be found https://ogmini.github.io/2025/10/06/Gmail-App-IMAP-Account-Attachments-Part-2.html. Once I “finish” tearing into IMAP artifacts in the Gmail App, I will write up a summary post/report.
I somehow missed this in yesterday’s post and it popped into my head on my commute to work this morning. We learned that a sent email that has attachments is stored differently in the Attachment table with a reference to a “cachedFile” which is a content link. In our test example we had:
Continuing to look at IMAP Account attachments from a previous post. Shifting gears for a moment away from looking the the lifecycle of digital photos. I wanted to verify my understanding of the folder structure for how attachments were stored. I had made a “informed” assumption that the attachment files are located at \data\com.google.android.gm\databases\{Account#}.db_att\{Attachment#}. Where the Account# and Attachment# come from the various database tables.
In my last few posts, I’ve been looking at the lifecycle of digital photos taken on an Android phone - https://ogmini.github.io/tags.html#Google-Photos. When researching and doing testing, it can be very useful to script as many steps as possible so that you can recreate testing quickly and consistently in different scenarios. I need to be able to easily pull the filesystem timestamps and MD5/SHA256 hashes along with the digital phones from an Android Phone. Spent a little time today throwing together a Python script to leverage various Android Debug Bridge (adb) commands.
Continuing from the previous post, I took some photos while the phone was in Airplane Mode to control when the photos were uploaded to Google Photos. I waited some time and disabled Airplane Mode and let the photos upload. I also wanted to see what happened if I just placed an image in the /storage/self/primary/DCIM/Camera location. Is there any sort of differentiation by Google Photos of images taken by the camera versus images just placed in the folder.
Recent events have resulted in my interest and examination of photos taken by an Android phone. What is the lifecycle of a typical photo taken by an Android phone with the Google Photos applilcation setup to backup photos to the owner’s Google account? What timestamps can we find? What are some potential indicators of timestomping or manipulation?
Now that I have a test Pixel 7 that has been rooted, I’m starting to dig into some Android forensics. Following from a previous post, I’m still looking at how third party IMAP Accounts are handled in the default Gmail application on Android 16. The below post is very in the moment so take everything with a grain of salt. My PR to ALEAPP was merged and I intend on improving it a bit as it resulted from artifacts from a CTF. There are plently more avenues to explore and document.
As I was poking around the filesystem of my Pixel 7 using adb shell, I was interested in examining the timestamps associated with the various files. In particular, I was looking at the image files taken by the built in camera and I wanted to see if I could correlate the filesystem timestamps with the EXIF timestamps. It appears that Android 16 uses some flavor of EXT4 and I set about researching EXT4 timestamps and came across this handy article - https://righteousit.com/2024/09/04/more-on-ext4-timestamps-and-timestomping/. The next question is if this translates over to Android 16.
Just finished “Anatomy of an Attack: Ransomware Workshop (IR224)” offered by CISA in coordination with Cybervance and Blue Cape Security. I talked about these in a previous post and would encourage those eligible to register.
Currently on a train heading somewhere fun and I will be disconnected from everything. It is important in this day and age to decompress and go touch grass. There will be no posts after this one until I get back.
Previously, we unlocked the bootloader on the Pixel 7 - https://ogmini.github.io/2025/09/09/Pixel-7-Unlocking-Bootloader.html. What follows are some of my notes on the process to patch init_boot using PixelFlasher/Magisk. This will give us root on the phone and allow us to take full backups for forensic analysis.
Making progress in rooting the Pixel 7 phone that I picked up. I spent some time today just unlocking the bootloader. Pretty straightfordward process at least for a Pixel device. What follows are some of my notes on the process to unlock the bootloader.
A few weeks back, I picked up a used Pixel 7 to use as a testbed to learn Android forensics. The intention is to root the phone, start poking around, and see where it leads me. Larger goal is to start contributing to ALEAPP. I specifically picked the Pixel 7 as it is a popular phone with a bootloader that is easily unlocked.
Following from Part 5, I wanted to test what happens if the TabState file is too large to natively fit into the MFT Entry. I opened Windows Notepad and typed some test text and repeatedly copy/pasted it back until it was sufficiently large. Took a memory dump and proceeded to analyze it using the same steps as outlined in Part 5.
August started strong and ended with chaos. Being in the ER for family is not fun; but all is well now. Minus some missed posts. We’re at the eighth month of the Zeltser Challenge from David Cowen and I’m still enjoying everything and it has really pushed me to go outside of my comfort area.
Let us recap what we’ve learned already and the process to manually recover Windows Notepad artifacts from memory. I am starting with a fresh memory dump for the scenario where we’ve opened a text file and made no changes. There are no other tabs. I had someone else create the scenario and memory dump so that I would not know anything about the text file that was opened.
In between prepping for my upcoming talk at BSides NYC, I’ve been slowly starting to learn how to write plugins for Volatility 3. I started with reading as much documentation and other writeups as possible on the process. These included:
I noticed during BelkaCTF 7 that ALEAPP didn’t extract all the emails as Belkasoft. This of course led me down the path of seeing how I could go about writing one and contributing it to the project. I actually wrote about this in yesterday’s post and how to recover the information manually.
Taking a break from Volatlity 3 and MemProcFS by doing some more preparation for my upcoming talk at BSides NYC. My rough draft consists of 8 slides including title, intro, and Q&A for a 25 minute talk. Should be a nice, succinct and informative talk. I need to make them look nicer and more engaging with color/pictures as they’re just currently textual talking points. I’m also incredibly nervous as this will be a day of many firsts:
I spent a little time today attempting to recreate my work in Volatlity 3 using MemProcFS. Helpful to see gaps/differences or possibly to see if I’m using a tool incorrectly. Initially, I found the absence of the settings.dat and Helium registry files in Volatility 3 to be a little odd. I figured that they would show up in the handles or filescan plugin. It is possible that filescan would find them; but I was getting an error about charmap and haven’t had the chance to troubleshoot.
Making more progress while reinforcing what I’ve learned in the past. What we saw yesterday was an MFT entry as evidenced by the “FILE0” at the start. Just to recap my goal for this research:
Yesterday I left off with the mystery of the missing TabState file and today I had a little time to dump the physical memory pages that are mapped to the notepad.exe process. To reduce the number of variables in the memory capture, I cleared out all the state and *.dat files associated with Windows Notepad and opened a test text file. The text file had the following contents:
A few months back, I had a post on using Volatility 3 to look at Windows Notepad. I had encountered issues with the symbol table and one thing that I had neglected/ignored was that the memory dump was acquired from a Hyper-V machine. I finally found some time to do some testing on a physical machine running Windows 11 23H2 and everything works as expected. I’m hoping to get a moment to test on a Windows 11 24H2 computer.
Been bouncing back and forth this weekend with @reece394 working on the ApplicationSettingsContainer. He has also been putting the plugin to use and came across an oddity relating to the RegUwpDateTimeOffset. You can follow and feel free to join the conversation at https://github.com/EricZimmerman/RegistryPlugins/pull/68.
Let us get into more detail about my previous post about poking around Windows Snipping Tool. Today, I’ll be focusing on two specific values being stored in the LocalState key in the settings.dat file which is located at %localappdata%\Packages\Microsoft.ScreenSketch_8wekyb3d8bbwe\Settings. The Windows Snipping tool has the option to automatically save any screenshots or recordings to a default location. This default location can be changed by the user. In the screenshot below, we can see that the screenshot location has been set to C:\Users\User\Desktop\SnipFolderTest\30 and the recording location has been set to C:\Users\User\Desktop\examine.
Yesterday, as I was diving into the Photos application in Windows with my registry plugin I noticed that there were subkeys to the LocalState key. I had not expected to see subkeys as nothing in the Microsoft documentation had led me to believe this was possible. I just ASSUMED it wasn’t possible. In the screenshot below, you can see an “Exp” subkey and subkeys to that subkey.
While working on the registry plugin to read the settings.dat files associated with various Windows packaged apps https://ogmini.github.io/2025/08/06/Registry-Plugin-Application-Settings-Container-(RECmd-and-Registry-Explorer).html, I did some testing against some other applications such as Snipping Tool and Photos. Much like Windows Notepad, these are default software on Windows 11. To put it bluntly, the plugin has already proved useful to me in looking for the various digital artifacts that these might leave behind.
I’ve been researching the settings.dat file that you will often find associated with various Windows packaged apps that might be distributed via the Windows Store or .msix files. You can see prior posts at https://ogmini.github.io/tags.html#Registryhive. Andrew Rathbun had suggested adding support to RECmd/Registry Plugins to be able to read these values. I’ve finally carved out some time to figure it out and I have a working Registry Plugin. Still need to finish handling some of the lesser used Value Types before I submit the PR.
Another month down and we had a few missed posts due to vacation just as I predicted in my last monthly accomplishment post.
That was a very quick turnaround from my previous post and opening an issue on the Velociraptor repository. There is now an official artifact from this commit by Mike Cohen.
My talk proposal was accepted a few days back! Excited and nervous at the same time. I’m not sure how much is appropriate to talk about yet; but I’m now focused on polishing my slides and material. I’ll definitely be practicing with some friends as an audience.
Just submitted an Artifact to the Velociraptor Artifact Exchange for Windows Notepad that leverages my WindowsNotepadParser. I’m pretty sure the YAML can be significantly improved. I’m hoping for some feedback and suggestions. It works fine; but requires creating a folder on the client to save the csv files. There should be a way to save them to the temp directory. I wasn’t able to get that to work though.
I encountered an interesting situation during BelkaCTF 7. This is not a writeup for one of the challenges but will give the solution as part of examining the oddity I experienced. I’m hoping that someone might be able to shed some light on the reason for the difference or if I did something incorrectly. One of the challenges required dumping a process from memory for further analysis. What is baffling is that I’m pretty sure that Belkasoft X uses Volatility 3 for processing memory images. But using Volatility 3 manually did not work for me. I ended up getting the right answer with MemProcFS.
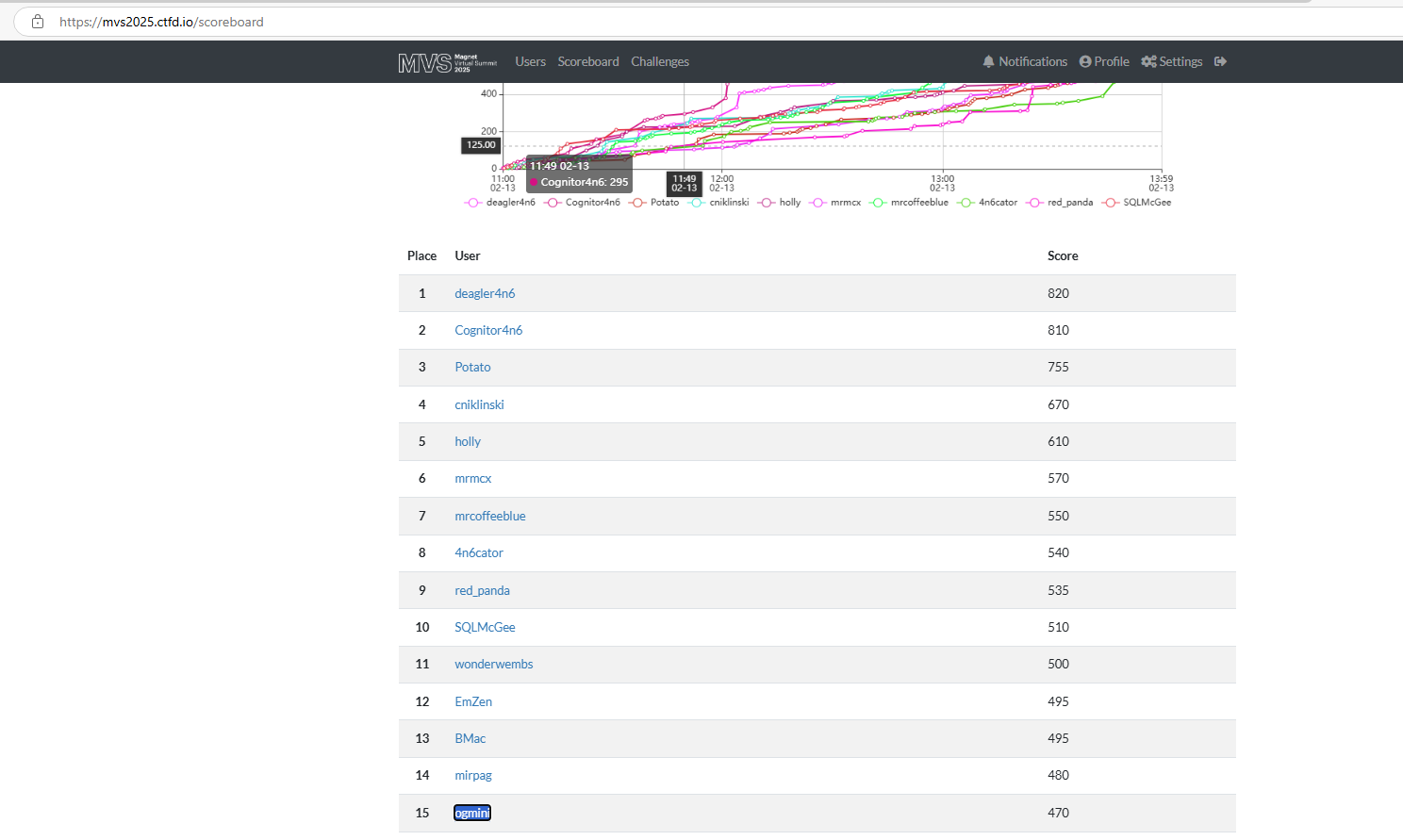
I think I’m done with the challenges. I have theories on how to attack some of them; but they aren’t working out. I’m currently sitting at 25 and the top individual from the USA on the scoreboard. I’m sure that will change as I sleep tonight. Looking forward to seeing the solutions and I will be posting my own writeups in the future. As always, there are multiple ways to solve a challenge.
Short post today as I’m in the middle of the BelkaCTF 7. Making slow progress in the challenges. I’m currently working on #7 which is listed as Hard. It definitely is… A little bit stumped on how to attack this one. Is it OSINT? Memory Analysis? API? I might have to skip this one. Looks like I’m in good company as 6 other people are at the same exact stage as me at the moment and a bunch of people have already skipped it.
Did a few of the tasks from a previous BelkaCTF as a warmup for this weekend. Solutions are written using Open Source or Free tools. I like to validate the findings from tools whenever possible. I’ve always appreciated that iLEAPP provides the location of where it found artifacts so that an analyst can manually parse if needed.
Running out of time to register at https://belkasoft.com/belkactf7/ for the BelkaCTF #7: Stranger Dfings on July 25th! As of writing this post, there are just under 1000 participants. I’ve prepped my workstation and I’m as ready as I’m ever going to be. On their LinkedIn page, they’ve dropped a few “warm up” tasks/hints from previous CTFs:
Today, I’m looking at Windows Notepad 11.2410.21.0 and comparing it to the previous version 11.2410.20.0. This could be useful if you somehow come across an older version of Windows Notepad on a system that is being investigated. For more details refer to https://github.com/ogmini/Notepad-State-Library.
Read some news about Mercedes Benz integrating Microsoft Teams, Intune, and CoPilot into MBUX/MB.OS. https://media.mercedes-benz.com/article/931e7af1-2d57-4e90-9e1e-252289e70648. Sounds like a very interesting research project for someone with both the money to buy a Mercedes-Benz CLA and the resources to tear one apart. See how it works, what could be exploited, and what digital artficats could be recovered.
Deadline for submission is July 19th, 2025. Just putting some last minute polish and reading over the description and outline. Imposter syndrome is kicking into high gear. I just need to remember that I’m just talking about MY experiences and MY thoughts on the subject. I am not trying to sell anything or convince anyone of anything.
So, our team has already finished the 6 challenges for the Hackers N’ Hops CTF. I stole sometime during vacation to participate as we collaboratively solved a few of them on Discord. When I get back, I’ll be attempting to solve the ones I didn’t do with them.
A few of us are participating in the Hackers N’ Hops CTF. A nice laid back CTF as they describe it. I like that there is plenty of time to participate. Ends on July 26th, so gives me time to give it a shot AFTER vacation. I might be tempted to poke at it though before I get back… One of my friends has already solved 2.
Continuation from Part 9 looking back at my coursework in the Master’s Degree in Digital Forensic Science. In this post, I’ll be talking about DFS-575 Digital Forensics for Civil Litigation.
CVE-2025-1727 was a fun one to learn about while on vacation. At least I didn’t take Amtrak to my destination. Neil Smith initially reported this back in 2012! He recently posted about this on July 11th, 2025 - https://xcancel.com/midwestneil/status/1943708133421101446.
While rereading the Microsoft Documentation on App Settings located https://learn.microsoft.com/en-us/windows/apps/design/app-settings/store-and-retrieve-app-data#versioning-your-app-data I took note of the ability to version application data. This is an optional feature and not a requirement but would be very useful if a program made changes to the structure of how application data is stored. Quoting the documentation:
I’ve got a lot of pokers in the fire right now. Some are personal challenges, some professional, some pure curiosity — but all of them are active. At any given moment, I’m juggling half a dozen tasks that feel urgent or important, or just too interesting to let go. So I figured I’d step back for a moment and write them all out — to share what I’m working on, and maybe to get a better handle on it myself.
A good reminder that we always, always need to test/verify. Looks like my assumption from a previous post about the identifier for each CompositeValue types was wrong! They do not ascend in order.
Spent today cleaning up the blog and fixing some Markdown syntax via Linting. All the tags should be fixed and working now. Also worked on updating the documentation on https://github.com/ogmini/Notepad-State-Library to be inline with all the research I’ve posted on this blog. One thing that I really need to finish is the Changelog for Windows Notepad that I left off with this post.
I’m pretty sure I can talk about this. At the end of 2024, I submitted my research on Windows Notepad to DFIR Review and made a post about it. I recently got notification that my submission was accepted!
NOTE This has been superseded by https://ogmini.github.io/2025/07/10/Registry-Hive-Data-Types-Part-8.html
OK, feeling more confident after today’s session. What I previously was calling a ValueLength seems to actually be the part that is telling me the data type. Below is this current work in progress. It still isn’t fully complete/right. Namely, I’m unsure how to correctly calculate the DataLength.
Unsure, if I’m making progress on the CompositeValues. I’m really stuck trying to figure out the structure. Last I left off I had the following theory:
Markdown Support is pretty limited in Windows Notepad. You have a toolbar at the top that lets you choose your formatting options. Most helpfully at the bottom is a toggle between “Formatted” and “Markdown Syntax”. This lets you see and manually write the Markdown syntax.
I tried to regression test Windows Notepad 11.2410.20.0 in relation to the replication steps from yesterday to see if I could get it to prompt to save.
Came across an interesting behavior while doing some testing. Initially, I wasn’t able to replicate it. Early on in I would sometimes see the creation of a guid.bin.tmp file in the TabState folder. At the time I had brushed it off as it would “resolve” by deleting itself and nothing seemed to break. I theorized that it might be related to file locks and Windows Notepad trying to protect the integrity of the TabState files.
Big milestone today, I’ve hit 6 months with no missed posts on the Zeltser Challenge. It is getting harder to find the free time to do research and write up posts as it is summer and the time for longer family vacations. July is going to be exceptionally challenging for this reason.
With the introduction of Markdown support we have a new setting in the settings.dat file to enable/disable the Formatting options. Using Registry Explorer we can take a look and see it:
Driving, especially on long road trips, is when I do some of my best thinking. The 6 hour trip home gave me a lot of time to think about that Windows Notepad. My mind wandered and contemplated about a few topics:
I picked a great time to go on vacation. Looks like my test system got the update (11.2504.62.0) for Windows Notepad that adds support for Markdown.
Came across a very succinct post about the “chain of RDP-related Event IDs” from Sujay Adkesar at https://thelocalh0st.github.io/posts/rdp/. They point out the importance of creating a narrative from logs and being able to visualize the timeline of events. I think this might be a fun standalone tool to write. I’m sure this ability probably already exists within various SIEMs and so forth.
Continuation from Part 8 looking back at my coursework in the Master’s Degree in Digital Forensic Science. In this post, I’ll be talking about DFS-570 Legal Principles of Digital Investigation.
Belkasoft is having their next CTF starting on July 25th, 2025. You can register and find more details at https://belkasoft.com/belkactf7/. I’ve registered and I’m looking forward to giving it a shot.
So yes, ended up quickly slamming out a not thoroughly tested pre-release of Window State Editor. You can find the application at https://github.com/ogmini/Notepad-State-Library/releases/tag/WindowStateEditor.
Had an issue submitted to the Notepad State Library repo asking how to reopen tabs that still exist as TabState files but are no longer present in the WindowState file. I had wondered if this was possible as there is a maximum number of supported tabs that you can have open in Windows Notepad. I have not actually tested this but it would make sense since the number of tabs is stored in the WindowState file as a LEB128.
Still stuck on the CompositeValue and this is a reminder that most of my posts are daily updates on what I’m working on. This is where I currently stand and I have a feeling the fix is easy and I’m just unsure on how to account for it within 010 Editor’s Binary Templates.
I realized today that I was pretty vague in my previous post about HOW I personally go about reverse engineering binary files such as settings.dat and the previous tab/window state files for Windows Notepad. I would love to hear from others about their methodology or any tips/tricks they have. I feel like this is somewhat of an inexact science with many different paths to get the same result. Some people may try to decompile or reverse engineer the executable that is writing to the binary file. Others may perform various tests and note what changes are seen in the binary files. What follows below is my methodology:
And we’re back online! I have a really simple program to help test and reverse engineer the settings.dat file. Helps me narrow down changes as I’m able to control the inputs by altering values and such. Quick snippet below for those interested. It isn’t anything fancy.
Currently, writing this with no power and internet. Luckily, I made progress earlier in the day with writing a testing/validation UWP application. The 36 data types lines up with what I’m seeing and testing. I’m still working on reverse engineering the Composite Value key.
While continuing to research the settings.dat file, I came across a Github repo specifically for editting settings.dat files related to UWP applications. Perusing the code revealed something interesting related the the Data Types I had spoken about yesterday. Previously, I had known of 4 from looking at Windows Notepad. The code actually outlines 36! https://github.com/ADeltaX/UWPSettingsEditor/blob/master/src/UWPSettingsEditor/Enums/DataTypeEnum.cs.
After yesterday’s post, I went back to reread what I consider the bible on the regf file format written by Joachim Metz. You can find it at https://github.com/libyal/libregf/blob/main/documentation/Windows%20NT%20Registry%20File%20(REGF)%20format.asciidoc. I find it is very useful to go back and reread documentation AFTER getting hands-on with the subject matter. You often can connect dots that you hadn’t previously and previously innocuous data will leap out at you as being very important.
Spent a few minutes today making an update to the RegistryHive.bt for 010 Editor. I had previously updated it to handle the application hive types described in this post. I had noticed that when using it to examine the settings.dat files for Windows Notepad it would sometimes throw an error on one test system but not another. It was attempting to read bytes at an address that did not exist. I’m unsure why the inconsistency and I want to dig into it a little more. It is possible the Binary Template isn’t completely handling the file correctly.
More of a thought exercise post on how UWP/Windows App SDK impacts the digital artifacts. It is Father’s Day today so a really quick post. UWP was deprecated in favor of the Windows App SDK - https://github.com/microsoft/WindowsAppSDK. One of the key features is MSIX which offers some nice features such as app containers. Quoting Microsoft here:
Microsoft has been updating Paint, Snipping Tool, and Notepad at a pretty good pace recently. Mainly pushing AI… You can read more about some recent future updates at https://blogs.windows.com/windows-insider/2025/05/22/paint-snipping-tool-and-notepad-updates-with-new-features-begin-rolling-out-to-windows-insiders/. All three of them are very similar in how they might store settings and other digital artifacts. This shouldn’t be a surprise as I believe they are all Windows App SDK or UWP based. Yesterday’s post, gave me a good reason to actually go take a quick look at Paint.
Yesterday, Chris Ray pointed me towards some more things they had observed in the User.dat. As he states, application registries do not care about the user disabling app launch tracking. It helpfully ignores the “Start_TrackProgs” registry setting. This results in some more useful digital artifacts.
Let’s keep this ball rolling! Two different things I’m still looking at in more detail to understand them as much as possible. The first was a reminder by @M4shl3 to look at the User.dat who recently left a comment on yesterday’s post. The second is more keys in the settings.dat that I had somehow missed previously or are new and a datapoint that isn’t so obvious depending on how you look at the file.
As is often the case, investigating something new leads to finding more new stuff that I hadn’t noticed before. The settings.dat application hive stores a few more digital artifacts that I had not documented previously. There are four more keys and a network/browser history artifact.
I need to get back to documenting the changes in Windows Notepad. I left off on version 11.2410.20.0 with my last post back on 4/27/2025. I’m going to skip ahead as Microsoft added a new “Recent Files” option. I have not yet identified which specific version introduced the change. I’ll go back to that project at some point.
Continuation from Part 7 looking back at my coursework in the Master’s Degree in Digital Forensic Science. In this post, I’ll be talking about DFS-560 Digital Forensics Encryption.
I saw a recent post by Oleg Afonin about the implications of how TRIM works on various SSDs. I would suggest reading his article as it dives into some very important distinctions when potentially imaging SSDs. It reminded me of a research article I came across during my classes at Champlain.
First and foremost, the June 2025 Public CTF from The DFIR Report was a very enlightening experience. It really highlighted a need to gain a deeper understanding of how to efficiently query Splunk or other SIEMs. I came into this with 0 prep and no experience beyond the theoretical and some classwork. The CTF centered around using your chosen SIEM which in my case was Splunk to investigate a cybersecurity incident. The DFIR Report classifies all their material as TLP:RED so I will only be speaking in generalities. I highly encourage anyone even remotely interested to try their Labs/CTFs. I had been on the fence about paying for their labs because it actually seemed to cheap. I was worried that it would provide no value or learning. If this CTF was any indication of the quality of their other labs. The value is immense.
Saw a post on LinkedIn from Kostas Tsialemis about their upcoming public CTF. I have read their site and contemplated entering one of their public CTFs in the past. Just never got the nerve to actually try it. Kostas was giving away 2 free entries and I ended up getting one. Thanks for the opportunity.
No major changes to Windows Notepad Parser. Yogesh Khatri helpfully pointed out that I had not actually documented the command line arguments and it appeared that the program would only work on a live machine. I thank him for opening an issue to point this out.
This is nothing new and has been around for years. But it is good practice to validate and try it yourself. You can retrieve the password(s) from *.rdg files using tools such as mimikatz and its various derivatives. I specifically tested with mimikatz against a test *.rdg file. As usual, I had to disable Windows Defender. The following command will reveal all:
The 2025 NYS Cybersecurity Conference has been great so far and there is still one more day of presentations. I’m going to digest everything a little bit before posting my thoughts and experiences. Instead, I’m going back to Remote Desktop Manager and the ability to store attachments or files to a connection. Again, maybe useful for storing a script or some other file. The Connections.db stores the information related to this artifact in the Attachment table.
Short post, just spent a few hours driving up to Albany, NY and I just checked into my hotel. All ready to attend the 2025 New York State Cybersecurity Conference. A lot of interesting talks and presentation.
Another month and I’ve been at the Zeltser Challenge for five months so far and still have not missed a post. The absence of David Cowen’s Sunday Funday challenges has made this a little more difficult. Though, it has forced me to channel my energy into other pursuits. Previously, I generally had a guaranteed topic or area to look at every week. I could choose to ignore it or attack it. So what happened in May?
As I continue to explore various tools such as Remote Desktop Manager. I feel it is very important to add to the existing knowledge base with open documentation and contributing to open source projects.
Had the pleasure of listening to some great talks at the online SANS - Ransomware Summit 2025. I particularly enjoyed the Hands-On Workshop put on by Mari DeGrazia titled “Forensic AI, Your Way: A Local LLM Installation”. The workshop we participated in is part of the SANS FOR563 course as a lab and you can find more information at https://for563.com/. My main takeaway is that a local LLM can be powerful when used appropriately.
Previously, I posted about logging the DPAPI activity and its relevance to RDCMan. I did not go into why and how this information would be useful.
Took a little bit longer than expected to finish the WinFE training and take the exam. I started this whole thing back on May 14th… https://ogmini.github.io/2025/05/14/WinFE-Training.html Got sidetracked a bunch looking at Remote Desktop Manager.
Followup to a previous post about logging DPAPI activity and verifying that RDCMan does leverage DPAPI/CryptProtectData to protect passwords. I’m happy to report that everything checks out and behaves as expected!
Had a lot of time to think during the Memorial Weekend holiday. My mind wandered to the naming scheme I have for system at home/work. It has changed over time from just leaving it at the default to funny names to role based names. How do you name your systems? Are your servers named after their roles? Are your computers named after their serial numbers? Are they completely randomized?
Another quick post as its Memorial Day weekend! I took a few minutes today to continue looking at what the master key actually encrypts. Yesterday we looked specifically at the tables related to Connections. Today, I’m looking at the tables related to documentation which I documented in Part 4.
Stealing 15 minutes away from the family weekend. Remote Desktop Manager supports the use of a master key for security. It encrypts the data sources https://docs.devolutions.net/rdm/commands/file/change-master-key/. What artifacts do we lose access to if the master key is set?
Quick post today as it is the start of the Memorial Day weekend! Remote Desktop Manager has the ability to add documentation to a connection. Useful for keeping notes, processes, and documentation in a place specifically related to that system. It is similar to a OneNote Notebook. The Connections.db stores the information related to this artifact in the following tables:
In the middle of finishing up a SQLMap for SQLECmd. Handy tool that can pull out targetted information from mapped SQLite databases and export them to CSV/JSON for ingestion by other tools such as Timeline Explorer. Pretty straightforward process and if you can write a SQL query, you can make a SQLMap for SQLECmd.
Busy day at work today. Didn’t have much bandwidth to poke around Remote Desktop Manager. I’ve always found it useful to utilize Database Diagrams to both understand and explain a database’s data structure. For SQLite databases, I use a tool called Dbeaver to easily auto-generate the Database Diagram for me and give me a good base to start better documentation. Oddly, I still prefer using SQLite Browser to examine the data. I’ve attached the generated image below.
I submitted a Kape Target for Remote Desktop Manager. I fully expect that I’ll be making changes to the Target even if it is to just update the documentation. Since yesterday’s post, I’ve found a few things that I missed/glossed over initially.
Remote Desktop Manager from Devolutions is an alternative to RDCMan that offers more features and centralized capabilities. You can read more about the them on their website - https://devolutions.net/remote-desktop-manager/. Today, I’ll be looking at version 2025.1.38.0 of the “Free edition” on Windows 11 24H2 to see what digital artifacts it leaves behind. For now, I’ll be using the default installation using the installer and not the standalone version.
Came across a post on LinkedIn recently about enable “Audit DPAPI Activity” in order to see event logs related to DPAPI calls. The post is coming from the standpoint of detecting anomalous actions in a SIEM or other tool.
Spent some of the day prepping for my CISSP exam. Still chipping away at the practice exam questions. I have to buckle down and just rip out the rest of the questions and schedule the exam. I know the material; just need the confidence.
Just submitted a Target to KapeFiles for ChatGPT Desktop. I realized one didn’t exist and I had done research into its artifacts for one of David Cowen’s Sunday Funday challenges. It will grab:
Just finished “Incident Response Triage - Mitigation (IR218)” offered by CISA. I talked about these in a previous post and would encourage those eligible to register.
Currently taking the WinFE from Brett Shavers. Today (5/14/2025) is the last day to take advantage of his great offer for free training! https://winfe.wordpress.com/2025/05/12/holy-smokes-free-winfe-training/. I haven’t completed the training yet; but I wanted to post some quick thoughts.
Had a little bit of time today to start an attempt at using Volatility to look at Windows Notepad. Sadly, I immediately encountered some issues and went into troubleshooting mode. I used both FTK Imager and DumpIt to obtain memory dumps from my test Windows 11 24H2 26100.3775 install just to make sure it wasn’t an issue with the tool I was using. I also downloaded an older Windows 11 sample memory dump from https://www.osforensics.com/tools/volatility-workbench.html. This loaded up fine in Volatility3 and I was able to examine it as expected. The windows.info plugin provided the information below:

Following up on yesterday’s post, I’ve started refreshing my knowledge and looking for useful articles on Volatility. I came across a Volatility 3 Cheatsheet from Ashley Pearson. I like the command comparisons between Volatility 2 and 3. There is of course Andrea Fortuna’s multiple articles on Volatility - https://andreafortuna.org/. I made extensive use of these during my coursework. If anyone has any other useful references, please share!
I’ve been wanting to dabble more with Volatility beyond the standard CTF or assignments that I had in my courses. I recently came across a post talking about using Volatility to recover text from Notepad (The old version) for a CTF Challenge. I think it would be a fun exercise to write a Volatility plugin to specifically scan and parse out the Unsaved Buffer Chunks from active Windows Notepad sessions.
Was poking around the Recent Virtual Group settings and it looks like I discovered a bug in the latest version (v3.1) of RDCMan. I’ve already reported it so hopefully it will get fixed. Would be a useful forensic artifact to have! It does work as expected on an older version of RDCMan that I still have (v2.93). So the below testing has been done on that version.
Just submitted a Target to KapeFiles for RDCMan. It will grab:
Andrew Rathbun pointed out an interesting anomaly that I didn’t pick up on related to the versioning. Sysinternals announced on their blog on 5/5/2025 that RDCMan v3.0 was released. The version listed on the documentation which was updated on 5/5/2025 was v3.1. Maybe just a quick stealth patch. Checking the executable shows the version as 3.1.0.0 and it reports as v3.1 from the About.
Going back many years, I’ve used RDCMan or Remote Desktop Connection Manager extensively as a Systems Administrator. The price was right ($free) and it had all the features I needed to easily be able to remote into multiple servers. It is now a part of Sysinternals and up to version 3.1 as of this post. This looks like an interesting application to research from a forensic investigation standpoint. What artifacts does it leave behind and what can be gleaned from its configuration files.
I follow Phill Moore’s great This Week in 4n6 weekly roundup as it is an awesome way to learn and keep up to date with various cybersecurity topics. I highly encourage you to follow his weekly roundups. His work is greatly appreciated. Maybe we should bring back webrings?
I came across a great writeup from Chris Ray over at Cyber Triage on ShimCache and AmCache. I made a post back on 4/20 about wanting to revisit various Windows Artifacts including ShimCache and AmCache. I really like Chris’s writeup because it is clear, organized, and easy to read. I would highly suggest reading it even just as a refresher.
Submitted my pull request to the KapeFiles Repository to add a Module that leverages my Windows Notepad Parser in a Live Response situation. First time writing a Module and hopefully won’t be my last contribution to that project. One of my favorite tools to use in my coursework and CTFs. Fingers crossed that it gets accepted and merged.
The fourth month of the Zeltser Challenge has been rather successful now that I’m looking back on my posts. I buckled down and finished reading all the material for the CISSP examination. I’m currently doing practice exams. I also participated and won three of David Cowen’s Sunday Funday Challenges:
Not a very interesting post today. Spent the evening doing some practice questions in the CISSP book. I always find the scenario questions with names and fake companies funny. I do like them though, as they are a good way realistic question/way for people to think about situations and how to handle them.
Releasing Version 1.0.4 of Windows Notepad Parser https://github.com/ogmini/Notepad-State-Library/releases/tag/v1.0.4. This is a bug/security fix release.
I’ve been listening/watching Hexordia’s Truth in Data Podcast on Youtube and the latest episode really resonated with my personal reasons for exploring DFIR. Jessica Hyde, Kim Bradley, and Debbie Garner interviewed Alexis Brignoni about open source code and how it relates to forensics. I’m going to pick out a few tidbits that jumped out at me. I do highly encourage everyone to give it a listen/watch. It is also on various podcast platforms in addition to Youtube.
With the impending delivery of my new Macbook Air, I’m compiling and reading resources on macOS forensics. I’d love it if anyone had any other suggestions for resources!
Today, I’m looking at Windows Notepad 11.2410.20.0 and comparing it to the previous version 11.2409.9.0. This could be useful if you somehow come across an older version of Windows Notepad on a system that is being investigated. For more details refer to https://github.com/ogmini/Notepad-State-Library.
Got my “Official Practice Tests” book from ISC2 this week and spent some time doing some questions today. I did not realize that it actually has 100 questions on the 8 domains AND four practice tests. I’m hoping to get through all the questions by mid-May with a goal of trying to schedule an exam for April. I recall that test times/dates fill up pretty quick around me when I scheduled my CSSLP exam.
Today, I’m looking at Windows Notepad 11.2409.9.0 and comparing it to the previous version 11.2408.12.0. This could be useful if you somehow come across an older version of Windows Notepad on a system that is being investigated. For more details refer to https://github.com/ogmini/Notepad-State-Library.
Continuing to document the version changes to Windows Notepad state files and today we’re comparing version 11.2407.9.0 to 11.2408.12.0. This could be useful if you somehow come across an older version of Windows Notepad on a system that is being investigated. For more details refer to https://github.com/ogmini/Notepad-State-Library. Unfortunately, I have been unable to track down the installer for 11.2404.10.0 and I don’t seem to have a VM Snapshot with that version. If anyone happens to have that version, please reach out!
During my initial research into Windows Notepad, I had noticed changes to the format of the state files and what was being stored or not stored in them. The initial version that I had torn apart was 11.2402.22.0. This post is the first part in going back to the previous versions and documenting changes. This could be useful if you somehow come across an older version of Windows Notepad on a system that is being investigated. For more details refer to https://github.com/ogmini/Notepad-State-Library. I will be documenting the changes from 11.2402.22.0 to 11.2407.9.0. Unfortunately, I have been unable to track down the installer for 11.2404.10.0 and I don’t seem to have a VM Snapshot with that version. If anyone happens to have that version, please reach out!

My 4/20 post has set me on a path to revisit Windows Artifacts. I’m going to start with revisiting Prefetch by looking at existing research to gain a base of understanding.

Short post for today as I’m enjoying the weather! I finished going over the all the material for the 8 domains on the CISSP exam. I’m currently doing practice questions and just ordered the official practice exams from ISC2. Once that book arrives, I plan on ripping through those and scheduling the exam.
Today, we look at HackBrowserData as part of the Sunday Funday Challenge. Nothing groundbreaking but a good exercise in double checking and verifying understanding and artifacts.
![]()
Today, we look at WebBrowserPassView from NirSoft as part of the Sunday Funday Challenge. Nothing groundbreaking but a good exercise in double checking and verifying understanding and artifacts.
Messing around with Windows Defender just to download and execute LaZagne locally leaves artifacts behind related to exclusions. There are of course other more stealthy ways to run LaZagne by using RATs such as Pupy or Meterpreter/Metasploit. This post will list out the Registry Keys and Event Logs related to Windows Defender.
Another week, another David Cowen Sunday Funday challenge posted at his blog and it is about looking for artifacts left behind by browser password extraction programs such as WebBrowserPassView.
Continuation from Part 6 looking back at my coursework in the Master’s Degree in Digital Forensic Science. In this post, I’ll be talking about DFS-550 Mobile Device Analysis.
Started looking into Kusto Query Language (KQL) in part due to a previous post/challenge on Cloud Log Delays. I would consider myself proficient with writing SQL queries and it has been a very useful skillset in my current career. The ability to quickly query large structured databases to report on or search for information has been a boon. Being able to whip up a query to answer a question about students—like “Which students are enrolled in all the courses required for their major but have not yet completed any elective courses, and what is their expected graduation date based on their current course load?”—never fails to elicit stares of awe.
Not much time today either and there is so much to look at. I was able to examine the com.docker.backend.exe.log file in a little more detail. This log is obviously meant for troubleshooting docker; but it contains a wealth of information with timestamps.
Getting some work done on this challenge; but I am not very confident that I’ll find much before the deadline. As a quick note for anyone else trying to run Docker or really anything that results in nested virtualization. You need to set ExposeVirtualizationExtensions to true for Hyper-V https://learn.microsoft.com/en-us/virtualization/hyper-v-on-windows/user-guide/nested-virtualization.
For every organization with important assets, there should be security/DR plans in place that are maintained, updated, and tested. As part of my recent role change to Interim CIO, I’m reviewing all of our security/DR plans with my team. Without going into much detail, all of our plans and information are documented but are a bit disjointed and in need of a polishing to make them easier to follow. It is handy that I’ve been studying for my CISSP certification as this exercise overlaps completely with the material. Knowledge in practice as they say. We are a small team in the grand scheme and I have to wear multiple hats including that of the CIO and CISO.
Another week, another David Cowen Sunday Funday challenge posted at his blog and it is about looking for artifacts left behind by using Windows Subsystem for Linux (WSL) to run a docker container.
OK, Domain 8 really is the CSSLP with a heavy emphasis on integrating security into the development process.
Domain 7 feels a bit like a rehash of my coursework. It focuses on managing incident reponses, preparation, disaster recovery, and business continuity. Pretty straightforward.
Continuing our roll on CISSP study with Domain 6 today. Would you believe that there is more overlap with the CSSLP again? This domain seems to really focus on how do you assess your security program and report on it.
I’m starting to sense a lot of overlap with the CSSLP material. Which makes sense though there is a slightly different viewpoint.
OSI, OSI, OSI! Domain 4 is at its heart about the OSI Model, its ramifications, implementations, and security implications. It hurts me that we still need to discuss technologies such as WEP. I’ve always been skeptical about the usage of Honeypots/Honeynets for normal businesses.
David Cowen has posted his weekly Sunday Funday challenge at his blog and it is about the looking at the delays present between action and log availability.
Domain 3 for the CISSP is a huge chunk of information and easily the longest chapter in my study book. Again, a mixture of subjects that I’m comfortable with and some that trend to the less comfortable.
The third month of the Zeltser Challenge has been tough as I’m fully getting into my role as CIO, restructuring the department, and getting acquainted with everything involved in this new role. This new role is very taxing mentally as I’m trying to juggle so many different projects, problems, and goals. Despite all this, I’ve still somehow managed kept to my daily post cadence.
I stalled out HARD in studying for my CISSP and my timeline fell apart. I had planned on being done with all 8 domains by this weekend and that is definitely not the case. I left off having finished Domains 1 and 2.
Last week I started poking around the network traffic generated by Windows Notepad when it makes calls to Rewrite. I made a post about what I found using Wireshark and mitmproxy. Part of the purpose of this blog is to push my knowledge by forcing me to actually DO and not just read and learn theory. That last post on mitmproxy and Wireshark was a perfect example of the DO. I had known that it was possible to setup a proxy to intecept and decrypt traffic. I even knew the general steps and tools required to analyze that traffic. What I never had was the need to put this knowledge to practice. I can now say that I’ve done it.
Continuing from yesterday’s post, we are looking at how to tell if someone is connected via SSH. I did not have time to look at SSH Tunnels. Please refer back to the main post for full details as this post will only talk about the tests and results.
Continuing from yesterday’s post, we are diving deep into the Windows Event Logs. Please refer back to the main post for full details as this post will only talk about the tests and results.
Continuing from yesterday’s post, we are testing for SSH artifacts when connecting to a Debian OpenSSH Server and a Windows 11 OpenSSH Server. Please refer back to the main post for full details as this post will only talk about the tests and results.
David Cowen has posted his weekly Sunday Funday challenge at his blog and it is related to his previous challenge on SSH Artifacts in Linux systems. I had posted that looking at SSH Artifacts in Windows would be a natural extension and here we are.
After releasing the first iteration of GaslitPad, I’ve been thinking about how to add some C2 or data transfer capability. The ideal case would be for the malware to send back information about opened files and more importantly, the unsaved buffer chunks as they are typed by the individual. You could essentially have a live window into the user’s notepad session and see what they are typing as they type it. Always funny to me that MS essentially has a keylogger built into Windows Notepad.
Continuation from Part 5 looking back at my coursework in the Master’s Degree in Digital Forensic Science. In this post, I’ll be talking about DFS-540 Malware Analysis.
Another successful entry/win to one of David Cowen’s Sunday Funday Challenges involving SSH in Linux https://www.hecfblog.com/2025/03/daily-blog-785-solution-saturday-32225.html. This of course begs the question, what artifacts are left by SSH on Windows 11 or other Windows flavors! Windows uses OpenSSH for the client and server implementations https://learn.microsoft.com/en-us/windows-server/administration/openssh/openssh-overview and this should make some of this research pretty straightforward when looking for artifacts specific to OpenSSH. Just as a quick example, the known_hosts file acts the same and is in essentially the same location as on Linux.
David Cowen has posted his weekly Sunday Funday challenge at his blog and I’m going to take a stab at it today.
In the world of Digital Forensics and Incident Response (DFIR), the line between traditional IT troubleshooting skills and forensic investigation isn’t as wide as it might seem. Both disciplines require a strong foundation in understanding system behavior, analyzing logs, and identifying the actions of users. A skilled IT professional is adept at navigating logs and system reports to identify irregularities, similar to a DFIR investigator who examines system artifacts, event logs, and network traffic to reconstruct incidents. The key similarity is the ability to trace actions across systems, understand what was done, and pinpoint where things went wrong. Whether it is identifying a user’s misstep during a hardware/software failure or determining the sequence of events leading to a security breach, both skill sets are rooted in keen investigative abilities and a methodical approach to troubleshooting.
Continuing from Part 4 on researching Windows Notepad - Rewrite. Taking a little detour and looking at the Correlation Vector. I don’t think this will be useful for anything; but I’ll doument what I’m seeing. Maybe someone will recognize this or knows more than me and can reach out with more details!
Progress has been made since Part 3 in relation to the network traffic and API calls. As we discovered earlier, Windows Notepad makes API calls to apsaiservices.microsoft.com using TLSv1.3. I’ve now successfully decrypted the calls and I’m making progress in understanding the traffic.
Continuation from Part 4 looking back at my coursework in the Master’s Degree in Digital Forensic Science. In this post, I’ll be talking about DFS-530 Incident Response and Network Forensics.
Short post today, continuing my research on Windows Notepad Rewrite https://ogmini.github.io/2025/03/14/Windows-Notepad-Rewrite-Part-2.html
Continuing with my writeups on my “fails” or the ones I just couldn’t figure out in the timeframe alloted. I want to talk about how I went about trying to solve the challenge and where I went wrong. This should help me in the future by highlighting weaknesses and areas for improvement. Each post will focus on just one “fail” challenge. You can find all my writeups page.
Continuing my research on Windows Notepad Rewrite https://ogmini.github.io/2025/03/08/Windows-Notepad-Rewrite.html.
Continuing with my writeups on my “fails” or the ones I just couldn’t figure out in the timeframe alloted. I want to talk about how I went about trying to solve the challenge and where I went wrong. This should help me in the future by highlighting weaknesses and areas for improvement. Each post will focus on just one “fail” challenge. You can find all my writeups page.
Continuing with my writeups on my “fails” or the ones I just couldn’t figure out in the timeframe alloted. I want to talk about how I went about trying to solve the challenge and where I went wrong. This should help me in the future by highlighting weaknesses and areas for improvement. Each post will focus on just one “fail” challenge. You can find all my writeups page.
Continuing with my writeups on my “fails” or the ones I just couldn’t figure out in the timeframe alloted. I want to talk about how I went about trying to solve the challenge and where I went wrong. This should help me in the future by highlighting weaknesses and areas for improvement. Each post will focus on just one “fail” challenge. You can find all my writeups page.
Continuing with my writeups on my “fails” or the ones I just couldn’t figure out in the timeframe alloted. I want to talk about how I went about trying to solve the challenge and where I went wrong. This should help me in the future by highlighting weaknesses and areas for improvement. Each post will focus on just one “fail” challenge. You can find all my writeups page.

Microsoft had previously added Rewrite to Windows Notepad on their dev release channels. It is now live to the public as of Windows Notepad Version 11.2412.16.0 and requires a subscription to Microsoft 365. I’ve already partially updated some of my documentation to note the new Application Hive entries related to Rewrite.
Found out about picoCTF a few days ago and decided to give it try with a few friends as a team. I would rank all of us as newcomers to CTFs. This competition is mainly meant for High Schoolers but is open to anyone to at least experience it. It runs from 3/7/2025 to 3/17/2025 so gives us a lot of time to take on the challenges in between our normal work. This is the first time I’ve formed a team to compete in one of these. We’re mainly just bouncing ideas off each other and sharing hints while indepedently tackling flags.
Releasing Version 1.0.3 of Windows Notepad Parser https://github.com/ogmini/Notepad-State-Library/releases/tag/v1.0.3. This is a pure bug fix release. The Windowstate CSV file wasn’t outputting the coordinates correctly.
Continuation from Part 3 looking back at my coursework in the Master’s Degree in Digital Forensic Science. In this post, I’ll be talking about DFS-520 Operating System Analysis.
 At least two solutions are possible.
At least two solutions are possible.
This second month of the Zeltser Challenge continues to be very fruitful and motivating. It has NOT been easy to post every day; but I still haven’t missed a post since the start.
 A child could solve it?!
A child could solve it?!
Continuing with my writeups on my “fails” or the ones I just couldn’t figure out in the timeframe alloted. I want to talk about how I went about trying to solve the challenge and where I went wrong. This should help me in the future by highlighting weaknesses and areas for improvement. Each post will focus on just one “fail” challenge. You can find all my writeups page.
 NASA has a SQLite DB on your Android Phone?
NASA has a SQLite DB on your Android Phone?
 That stegosaurus hid something from us!
That stegosaurus hid something from us!
Continuing with my writeups on my “fails” or the ones I just couldn’t figure out in the timeframe alloted. I want to talk about how I went about trying to solve the challenge and where I went wrong. This should help me in the future by highlighting weaknesses and areas for improvement. Each post will focus on just one “fail” challenge. You can find all my writeups page.
 There is a smaller Operating System inside!
There is a smaller Operating System inside!
Continuing with my writeups on my “fails” or the ones I just couldn’t figure out in the timeframe alloted. I want to talk about how I went about trying to solve the challenge and where I went wrong. This should help me in the future by highlighting weaknesses and areas for improvement. Each post will focus on just one “fail” challenge.
I’m going to flip the script for the typical writeups you see for CTFs and talk specifically about my “fails” or the ones I just couldn’t figure out in the timeframe alloted. I want to talk about how I went about trying to solve the challenge and where I went wrong. This should help me in the future by highlighting weaknesses and areas for improvement. Each post will focus on just one “fail” challenge.
Continuing from Part 2, the existence of the History folder threw me for a bit of a loop as I use other tools such as Git or TFS to handle versioning and history. There is a setting under Workbench related to Local History that is enabled by default. You can see the options in the screenshot below.
Looks like Andrew Rathburn had already created a Target for Windows Notepad! I somehow didn’t notice it because I only checked the Apps folder and not the Windows folder. I’ve updated it to pull the Window State *.bin files and the settings.dat Application Registry file. I also added a link to my documentation on the file format and behavior.
Finally got a few minutes to start working on writing the KAPE Target for Windows Notepad. It will grab the Tab State, Window State, and settings.dat files that I’ve talked about in my research. Pretty straightforward process and I just want to do a little more testing and make sure I have everything right before I submit a Pull Request.
Releasing Version 1.0.2 of Windows Notepad Parser https://github.com/ogmini/Notepad-State-Library/releases/tag/v1.0.2. This new version includes a .NET 8.0 dependent version and a standalone version that doesn’t need .NET 8.0 installed on the system. There is also a minimal branch that doesn’t include the ability to generate a GIF from the changes. The noticeable change is some formatting of the CSV files to reorder and remove unnecessary columns.

Continuation from Part 2 looking back at my coursework in the Master’s Degree in Digital Forensic Science. In this post, I’ll be talking about DFS-510 Scripting for Digital Forensic.
Still banging my head with the 2025 Magnet CTF and was able to solve a few more today. Let us get back to investigating Visual Studio Code!
I’ve begun to look at Visual Studio Code in my quest to document useful digital artifacts in various text editors. In a similar fashion to Windows Notepad and Notepad++, Visual Studio Code will keep unsaved content between sessions. After documenting what I can find I will use that knowledge to see how one might attack Visual Studio Code. Another project is slowly building in my head to write a unified application to attack text editors and their data.
It is always interesting to look at two different approaches to the same problem. Both Windows Notepad and Notepad++ are at their core text editors that support tabs and have the ability to keep unsaved changes between sessions. How they approach these features differ and we’ll be talking about how these manifest themselves in the digital artifacts.
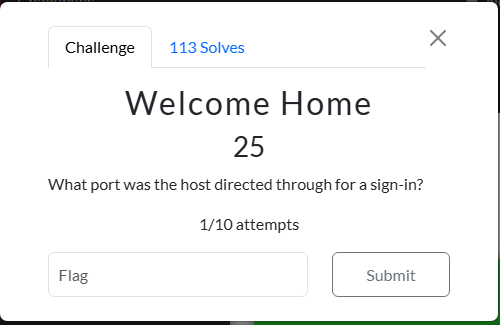
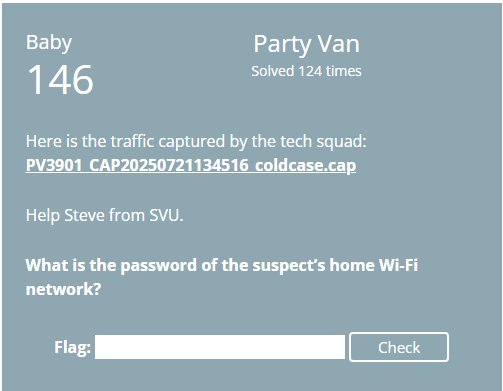
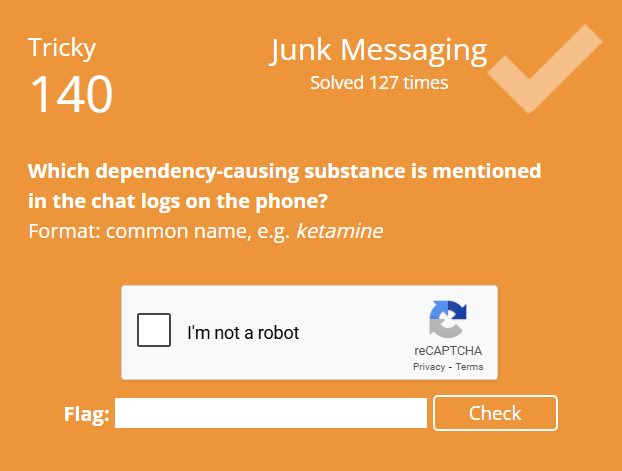
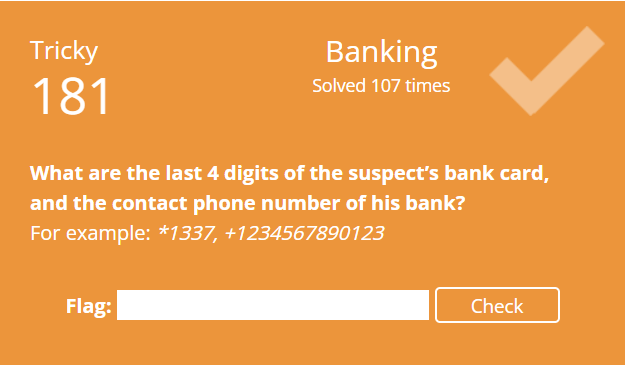
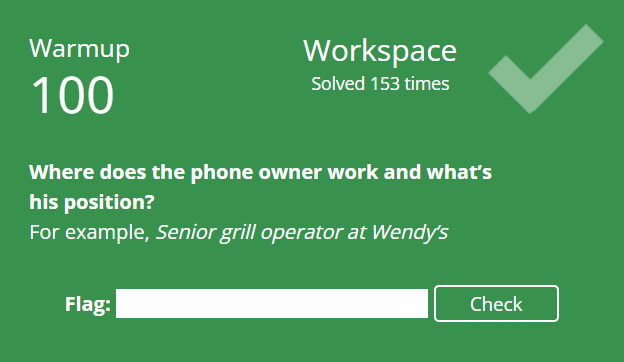
I gather during CTFs you should be operating under tight OPSEC in order to win. I’m not though! So what follows is a quick writeup of my pre-analysis of the provided images.
It is CTF time!
David Cowen recently introduced me to Cursor which is an AI Code Editor and he has a few posts on his blog about using it that you can find page. I wanted to play around with this and my recent work on researching Notepad++ gave me a good excuse as it provided a target that wasn’t too complex.
I think I’m done researching what digital artifacts can be retrieved from Notepad++. I’ve been able to confirm/validate the findings from Forensafe and I will be providing more detailed information about them below. As I stated in Part 1, there is no real complication to the digital artifacts and everything is human readable with any text editor. In a future post, I will be pointing out how Windows Notepad and Notepad++ achieve similar functionality while storing the information differently.
Stemming from my research into Windows Notepad, I think it would be fun to take a look at Notepad++ and maybe other text editors like Visual Studio Code to see what kind of digital artifacts we can uncover. Personally, I use Notepad++ and I’m sure it is a very popular text editor for many other people. I’m sure others have already looked and I’ve found information from Forensafe mainly showing how their tool can recover information. They didn’t go into many details on the page and I think it would be worthwhile to document that more fully in the open for all to see. It is also possible that changes have been made to Notepad++ since the article.

Just finished “Preventing Web and Email Server Attacks (IR205) offered by CISA. I talked about these in a previous post and would encourage those eligible to register.
After completing the Windows Forensics with Belkasoft certification, I learned that Belkasoft has a bunch of different CTF challenges that are still available to practice and hone my skills. I also want to use this as an opportunity to improve my report writing and presentation skills. It is one thing to find evidence and another to present it to a non-technical audience. The plan is to start on the first one and just make my way through the list. You can find their CTFs at https://belkasoft.com/ctf.
Got the results back from the Belkasoft Windows Forensics course/exam and I passed. I already gave my thoughts on the actual course https://ogmini.github.io/2025/01/25/Belkasoft-Windows-Forenics-Part-2.html.
I’ve started studying for the CISSP exam and what follows are a recap and notes on Domains 1 and 2. So far, I’m finding the material pretty straightforward and things that I’m already doing in my professional life. As everyone says, you need to think like a management for this certification and I already do.
The first month of the Zeltser Challenge issued by David Cowen has been very educational and challenging! I have not missed a day though I totally threw my posting topic “plan” out the window and it has ended up being far more organic and closer to a diary of what I’m working on. So far, I know of the following fellow participants:
Yesterday I posted about the plan to release GaslitPad next week and some of the future capabilities I wanted to implement. I ended up adding the “inverted” attack which I’m now calling the “Sleep Attack”. So that will be available in the first release. Just a reminder, this POC Malware makes no attempts at obfuscation or hiding its actions.
I’ll be releasing my POC Malware called GaslitPad sometime next week. Please see my previous post for some background. I’ll lead off with a video demonstration - https://www.youtube.com/watch?v=z-5MxRxgBxI. GaslitPad makes no attempts at obfuscation as it is purely a proof of concept.
LevelDB utilizes CRC32 for data integrity checks; but it doesn’t use the normal CRC32 algorithm. Reading the code comments it utilizes a masked representation of CRC32 because it is problematic to compute the CRC of a string that contains embedded CRCs. The code accomplishes this by rotating right by 15 bits and adding a constant of 0xa282ead8ul.
Continuing work on the binary template file for the LevelDB .ldb files. Learning a lot and pushing my knowledge boundaries. I am definitely recreating prior research; but I find this is the best way to learn and also validate previous findings. It is also possible things have changed.
Just attended Introduction to Log Management(IR210) offered by CISA. I talked about these in a previous post and would encourage those eligible to register.
Continuing my analysis of the ChatGPT Desktop App by creating binary template files to help me understand the LevelDB and IndexedDB databases. I personally find it useful to “visually” see the binary files structured in hex editors like 010 Editor and ImHex. It helps me know if I’m on the right track and it is pretty easy to later convert that to code for a tool.
Time to get serious and study to pass the CISSP examination. Outlining my plan and giving myself a deadline will keep me motivated and on track. I picked up a copy of Destination CISSP 2nd Edition to serve as my study material since it had been updated for the revised exam.
Started on the Windows Forensics course from Belkasoft and I was happy to see that they explicitly mention that you can use other tools besides Belkasoft X. I did use Belkasoft X to work on the problems in order to get familiar and learn the software. What follows are some quick thoughts.
Belkasoft is offering a free course and certification on Windows Forensics using their software. More details can be found at this link - https://belkasoft.com/windows-forensics-training. It also provides 6 CPE credits. I just signed up and I’m hoping to complete the course this weekend. The content is obviously centered around using their tools and should be a nice introduction to them. I intend on using other free tools to get the same results. I’ve personally found it very educating to use multiple tools to retrieve and view artifacts from different lenses. After I complete the course, I’ll be posting about my impressions and thoughts.
Continuing my work on David Cowen’s Sunday Funday challenge, I leveraged ChromeCacheView and ChromeHistoryView to look both at the Edge Browser and the ChatGPT Desktop App. I want to see if we can capture the user authentication process with timestamps and any artifacts related to uploaded files.
Continuing from an earlier https://ogmini.github.io/2025/01/21/Deep-Dive-LevelDB.html, I’ve had a chance to quickly try out two different tools on LevelDB databases used by the ChatGPT Desktop App.
While investigating the ChatGPT Desktop application in yesterday’s post, I came across an Electron App leveraging LevelDB databases. That of course led me to search for tools and research to help me parse and understand the LevelDB files.
My submission to another one of David Cowen’s Sunday Funday challenges. This time related to the ChatGPT Desktop Application. https://www.hecfblog.com/2025/01/daily-blog-723-sunday-funday-11925.html
It has been a busy week with multiple big changes on the horizon. Definitely feel like I have too many irons in the fire. Hopefully by next month, I can talk about them. Still fighting that imposter syndrome. What have I been able to accomplish this week though?
Parts have started to arrive for the next iteration of my next server. I’ll be keeping the same software stack as the current server and obviously repurposing the current server for other duties. In Part 3, I’ll talk about the thought process that led me to this configuration and what other options I investigated.
I’ve had a few free moments to test out MSLab and it seems very promising. By just downloading the scripts, two ISOs, and modifying 2 lines in a configuration script I was able to spin up a virtual network with a Server 2025 Domain Controller and two Windows 11 client machines that are already joined to the domain. When I’m done with the lab, I can just run the cleanup script and it removes all the VMs from Hyper-V. Redeploying the exact same lab again just requires running the deploy script with the appropriate configuration.
Just attended Preventing DNS Infrastructure Tampering (IR206) offered by CISA. I talked about these in a previous post and would encourage those eligible to register.
I am in the process of planning and building my next hypervisor for use in my homelab. Looking for infrastructure as code or scripting options to easily spin up test labs is proving to be an interesting journey. There are the standard options of Terraform, Ansible, Vagrant, and the various cloud vendor specific implementations.
Continuation from Part 1 looking back at my coursework in the Master’s Degree in Digital Forensic Science. In this post, I’ll be talking about my second course at Champlain College.
David Cowen has started up his Sunday Funday challenges again and his latest one is related to SRUM. You can find his challenge on his blog.
I’ve always run a few personal “servers” at home running simple services like Plex, file storage, etc. When I started my Master’s Degree, I wanted to setup a server to run Hyper-V so that I could keep all my coursework contained, backed up, and I could easily spin up VMs for exploration. Utilizing tailscale allowed me to access these VMs anytime, anywhere giving me the ability to easily work on assignments while on vacation or travelling.
What Hex Editor(s) do you prefer to use?
I’m looking for some advice on how to automate regression testing for forensics software. As I researched Windows Notepad, Microsoft continually updated and made changes to how the binary files worked. I touched upon this issue in a previous post https://ogmini.github.io/2024/11/27/Microsoft-Store-Older-Versions.html.
Today, I was talking to a few people about the PowerSchool hack and the question was posed, “Why would anyone want student data?”. I was taken aback. In this post, I want to explore that question and give reasons why a threat actor would want this data with some hypothetical scenarios.
Yesterday news hit that Powerschool was hacked resulting in a threat actor stealing student and teacher data. Powerschool provides SIS platform software to K-12 schools. Bleeping Computer has a good article on the incident - https://www.bleepingcomputer.com/news/security/powerschool-hack-exposes-student-teacher-data-from-k-12-districts/.
Just attended Defend Against Ransomware Attacks Cyber Range Training (IR209) offered by CISA. I talked about these in a previous post and would encourage those eligible to register. As always, the course was full of information with the added benefit of a virtual environment to play around in. I’m always amazed at how much they can pack into so little time. I only wish it was a full day course.
January 2022, I started my first course at Champlain College to complete my Master’s Degree in Digital Forensic Science. I’ll be making a few posts related to my experience with the coursework and my takeaways. It’s important to remember that everyone entering this program came from diverse professional and personal backgrounds. This diversity was both a strength and a challenge. On one hand, it sparked valuable discussions and brought differing viewpoints. On the other hand, students had widely varying expectations and skill levels, which led to inconsistencies in the perceived difficulty and usefulness of the courses. I mention this as my background will influence my viewpoint and my experience is and will be different from others. These posts are not meant to be a review of the program; but a recap of my experience and learning.
When David Cowen posed this challenge for 2025, I knew it wouldn’t be easy. I may have underestimated how hard it would be though…
The main certification I want to complete for early 2025 is my CISSP after having already obtained my CSSLP certification in 2024. Hopefully, these weekly blog posts will help keep me on track and making forward progress towards that goal. I’ve already picked up my copy of Destination CISSP.
Gaslitpad is the name of the POC malware that I’m currently working on. It is the result of my ongoing research into Windows Notepad at https://github.com/ogmini/Notepad-State-Library. The general idea is a program that sits in wait and changes the unsaved buffer for nefarious purposes.
How do you make the time to compete in CTFs?
Happy New Year and welcome to 2025!
What follows is my submission to DFIR Review. I figured I should post this on my Blog while it is under review.
Have you ever needed a previous version of an application from the Microsoft Store?
This blog will document my exploration of Digital Forensics and Incident Response (DFIR) as I make the transition into this exciting field. More importantly, it will serve as a centralized place to store my notes, observations, and learnings.