ogmini - Exploration of DFIR
Having fun while learning about and pivoting into the world of DFIR.
About Blog Posts by Tags Research Talks/Presentations GitHub RSS
David Cowen Sunday Funday Challenge - Browser Password Extraction Evidence (HackBrowserData)
by ogmini
Today, we look at HackBrowserData as part of the Sunday Funday Challenge. Nothing groundbreaking but a good exercise in double checking and verifying understanding and artifacts.
HackBrowserData
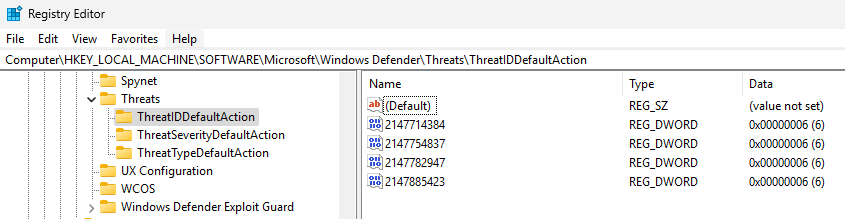
Windows Defender REALLY does not like this executable. Just downloading the release from the GitHub required adding two seperate Allowed Threat exceptions. Again, we see similar Event Logs to LaZagne of detecting the threat, quarantining the threat, and allowing the threat.
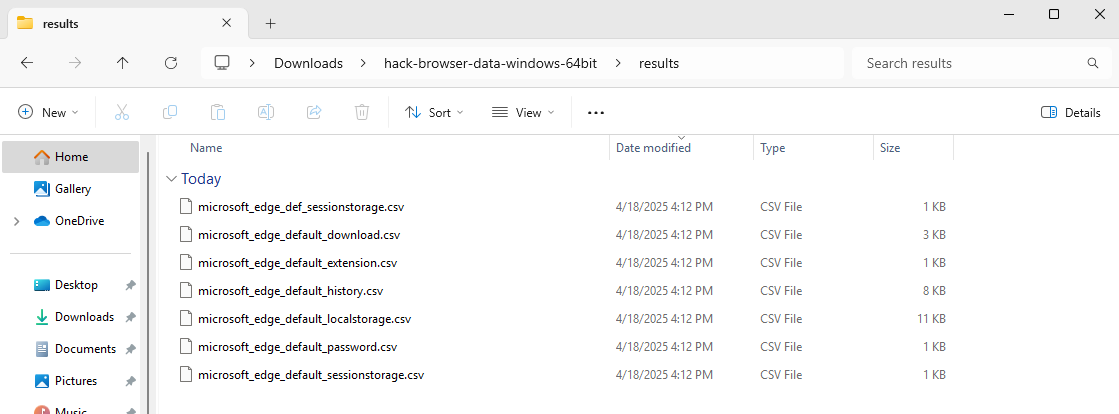
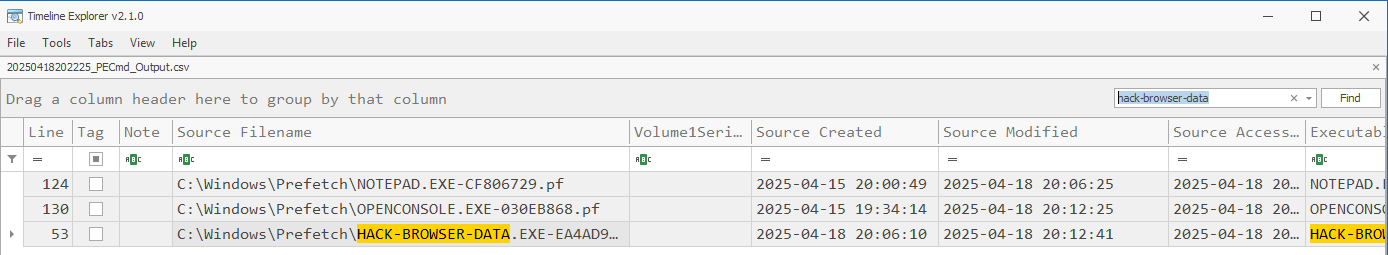
Every time HackBrowserData is executed, it will create/update csv files in a results folder. The MAC Timestamps for this file can prove useful as it potentially shows first execution by looking at the folder and the last execution by looking at the csv files. In this test I just ran the executable from Windows Explorer the same way that WebBrowserPassView was tested.
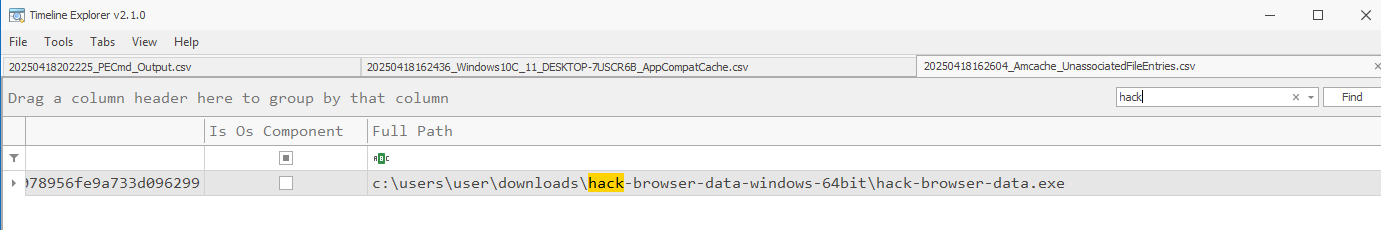
There are artifacts to be found in the Prefetch and Amcache, All the standard caveats apply to these artifacts and much research has already been published on them. I’ll provide some links in the References section below.
References
Shimcache - 13Cubed
Prefetch - 13Cubed
Shimcache and Amcache - Magnet Forensics
MUICache -13Cubed