ogmini - Exploration of DFIR
Having fun while learning about and pivoting into the world of DFIR.
About Blog Posts by Tags Research Talks/Presentations GitHub RSS
BelkaCTF 7 - AAR Workspace
by ogmini
We need to find out where the owner of the phone works and their position. From the previous task, we have some areas to examine that might find us our answer:
- Email boxes related to
googleslover93@gmail.comandstonepresspa@runbox.com - Telegram
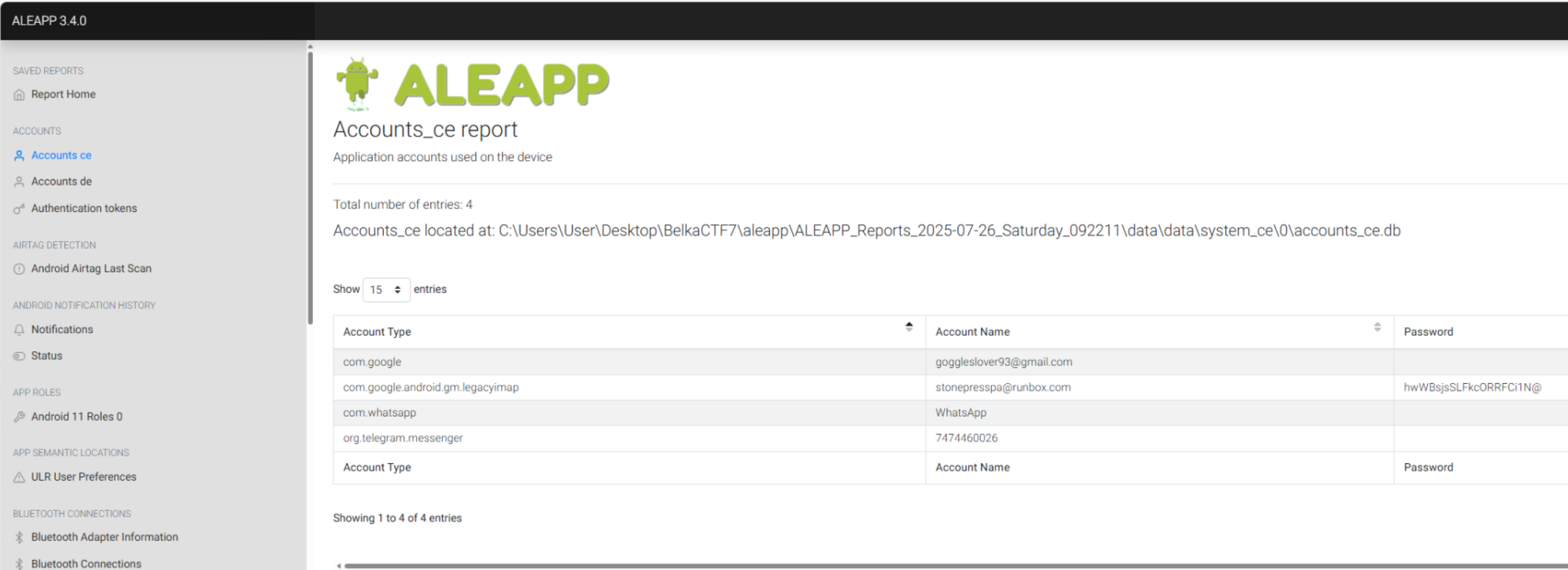
Always worth browsing any communications on a device as a very early step. Unfortunately, ALEAPP doesn’t appear to be able to retrieve the digital artifacts for the stonepresspa@runbox.com mailbox so we must go digging manually.
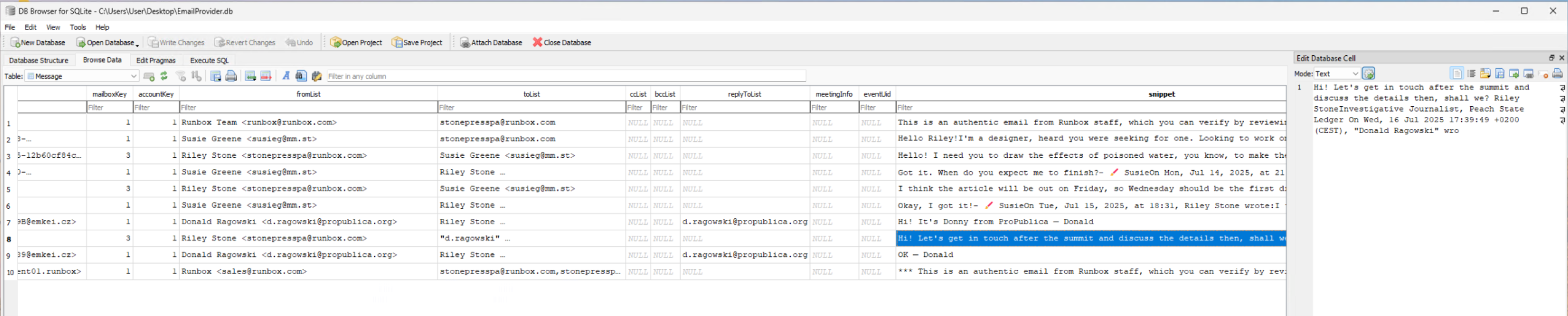
Navigating to \data\com.google.android.gm\databases we come find an EmailProviders.db file which we can open up in DB Browser for SQLite. Looking at the Message table, we find an email sent from stonepresspa@runbox.com to a d.ragowski@propublica.org and in the body it contains the name of the workplace and their position.
Investgative Journalist
Peach State Ledger
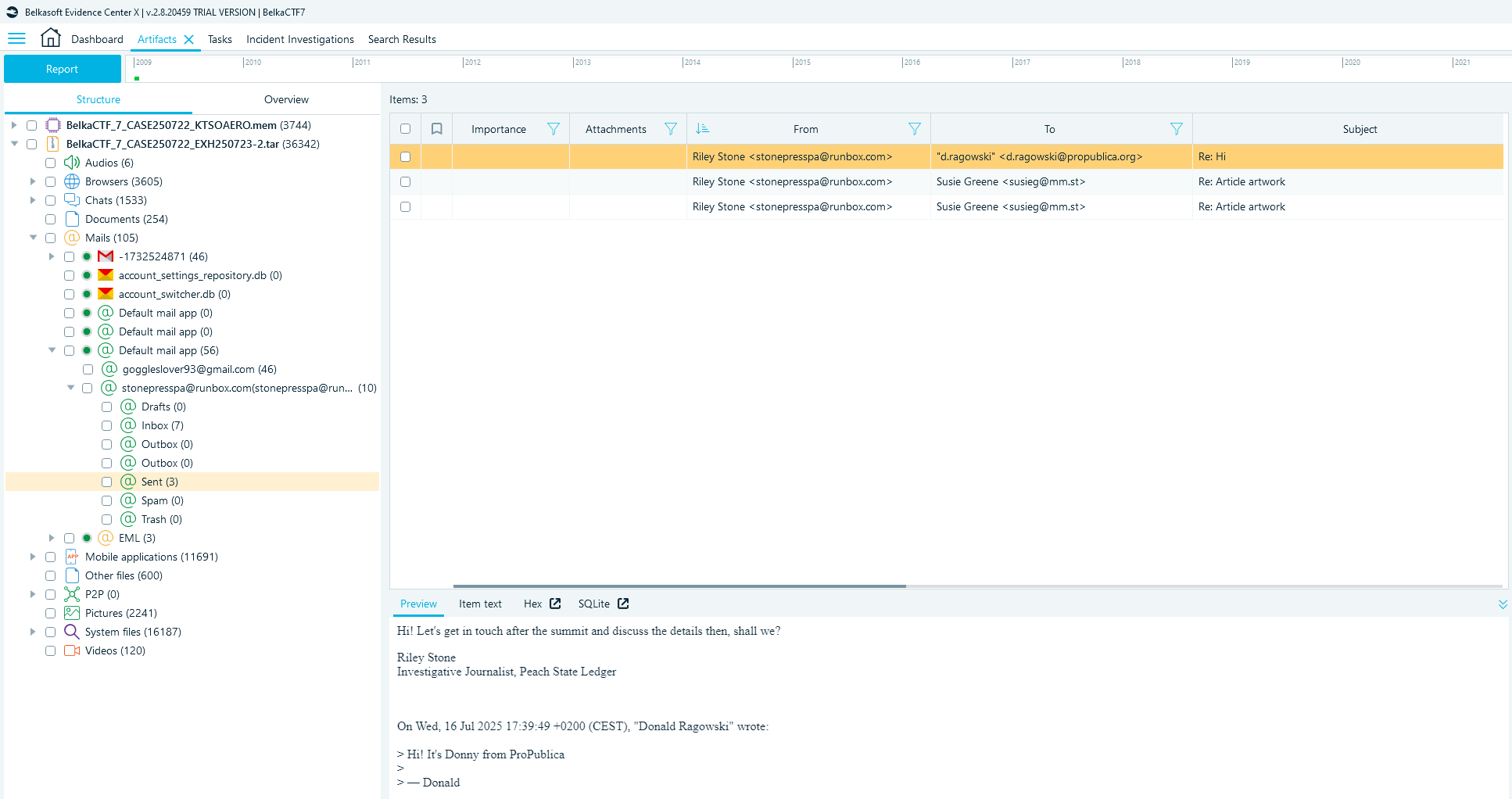
Using BelkaSoft was much easier as it finds the IMAP mailbox and parses out the Sent emails from the database.
Thoughts
Always good to verify. I’m actually surprised that ALEAPP didn’t parse out this artifact. Maybe something to contribute as a plugin.
tags: #CTF #Belkasoft #Writeups