ogmini - Exploration of DFIR
Having fun while learning about and pivoting into the world of DFIR.
About Blog Posts by Tags Research Talks/Presentations GitHub RSS
Memory Forensics - Windows Notepad Part 2
by ogmini
Yesterday I left off with the mystery of the missing TabState file and today I had a little time to dump the physical memory pages that are mapped to the notepad.exe process. To reduce the number of variables in the memory capture, I cleared out all the state and *.dat files associated with Windows Notepad and opened a test text file. The text file had the following contents:
supercalifragilisticexpialidocious file saved
I’m not going to retread the steps I took in Part 1.
In order to dump the memory pages of notepad.exe I used the memmap plugin.
vol -f "memdump.mem" windows.memmap --pid 5632 --dump
Popping the resulting *.dmp file into 010 Editor and searching for our text gets a hit. Below is a screenshot of the relevant section.
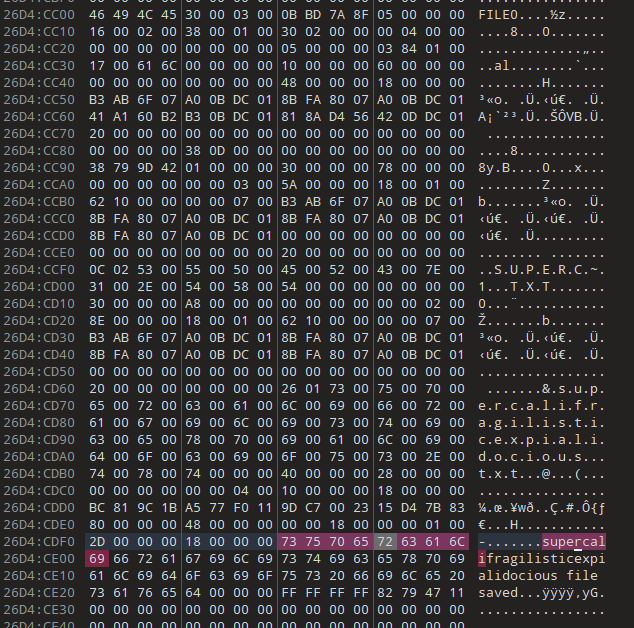
Making progress.
Next Steps
Next steps are to make sense of and understand that section. I can definitely see the contents of the file and what appears to be the filename and the short filename version https://en.wikipedia.org/wiki/8.3_filename.
tags: #Volatility #Memory-Forensics #Windows-Notepad #MemProcFS