ogmini - Exploration of DFIR
Having fun while learning about and pivoting into the world of DFIR.
About Blog Posts by Tags Research Talks/Presentations GitHub RSS
Memory Forensics - Windows Notepad Part 3
by ogmini
Making more progress while reinforcing what I’ve learned in the past. What we saw yesterday was an MFT entry as evidenced by the “FILE0” at the start. Just to recap my goal for this research:
After capturing a memory dump from a live system with an active notepad.exe process. I want to recover/recreate the state of Windows Notepad as much as possible. Automate the process in some fashion.
I’m happy to say that from preliminary examination, I have done this manually on a test memory dump. General steps are:
- Determine PID of notepad.exe process. It is possible to have multiple notepad.exe processes and this process will need to be done for all of them.
- Find any handles related to the TabState/WindowState files.
- Dump the TabState/WindowState files
- Examine the WindowState files and compare to dumped TabState files. This identifies any missing TabState files and their GUIDs.
- Dump the memory pages of the notepad.exe process.
- Search the MFT entries for any with a filename matching the GUID from before.
- Recover/examine the missing TabState file for filename/path
- Search the MFT entries again for that file.
- Profit
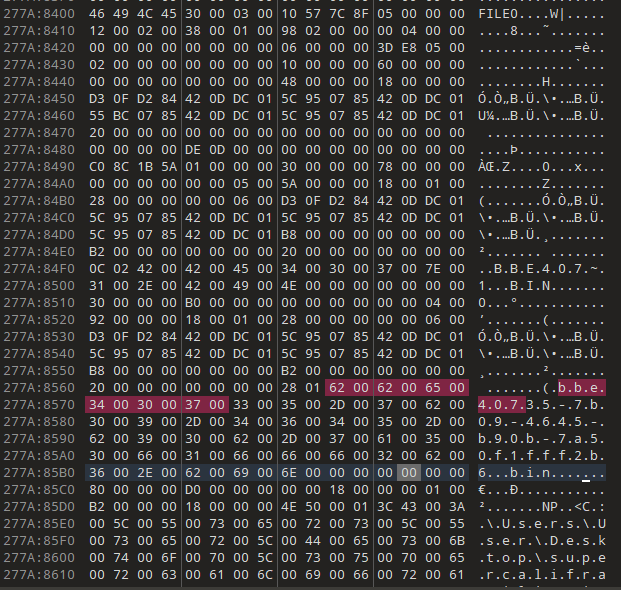
Screenshot of the MFT entry for a missing TabState file. You can see at the bottom the path to the original file.
Next Steps
Automate this somehow. I also need to test with a larger text file to see how the MFT entries react.
tags: #Volatility #Memory-Forensics #Windows-Notepad #MemProcFS