ogmini - Exploration of DFIR
Having fun while learning about and pivoting into the world of DFIR.
About Blog Posts by Tags Research Talks/Presentations GitHub RSS
BelkaCTF 7 - AAR Metamorphosis
by ogmini
The suspect’s body started acting weird… People(Is our suspect people?) often use health monitoring apps/devices connected to their phone. Heading back over to ALEAPP, I check out the Installed Apps (Vending) https://forensafe.com/blogs/Android_InstalledApps.html and do a search for “health” to see what we find. It is important to remember that this search won’t always work as there is no requirement for the package name to make sense. I got lucky here.

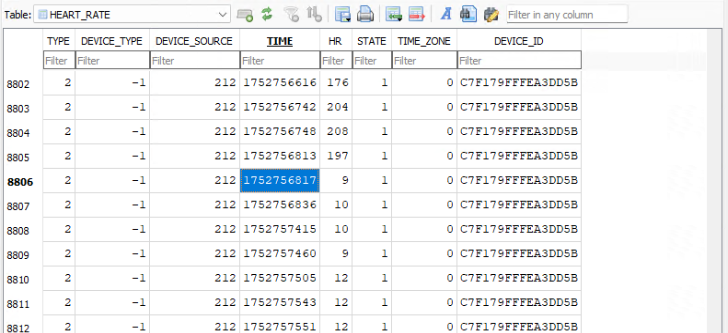
From here, I start poking around the \data\data\com.xiaomi.hm.health\databases folder that is associated with the application. After opening various database files in DB Browser for SQLite, I find an interesting one called origin_db_ef2042f8ec65801481fb688859d4e279 which has a table named “HEALTH_RATE” with TIME and HR columns. Appears that TIME is a timestamp and HR would be Heart Rate. Scrolling though the records a drop in Heart Rate is noticed at 1752756817 or 2025-07-17 12:53:57 UTC.
Thoughts
Our suspect effectively died with a heart rate of 10 bpm. Belkasoft X is able to parse this artifact natively. Shortly after the CTF, support for this artifact was also added to ALEAPP by its5q via https://github.com/abrignoni/ALEAPP/pull/584.
tags: #CTF #Belkasoft #Writeups